Identity lifecycle management presents a number of challenges: You need to quickly onboard employees so that they have access to the applications needed to do their jobs, you need to immediately offboard them when they leave the organization so they’re not a security threat, and you need to ensure IT isn’t bogged down with all changes in between as employees shift roles, get promoted, change locations, and so on.
Identity Automation Blog
Blog Categories
- Cybersecurity (134)
- Company News (101)
- K-12 Education (80)
- RapidIdentity (71)
- Multi-Factor Authentication (69)
- Higher Education (44)
- Identity Governance (43)
- Identity Lifecycle Management (32)
- Single Sign-On (32)
- Healthcare (29)
- Access Management (19)
- Government & Public Sector (5)
- Identity Automation Pathfinder (1)
Recent Posts by Kathleen Garska
Two-Factor Authentication (2FA) Explained: Social Login
Companies and end-users alike are constantly looking for authentication methods that lower barriers to entry and improve user experience without compromising security.
Healthcare Cybersecurity and the Human Factor: Using Risk-Based Authentication that Considers Behavioral Factors
In the healthcare industry, a lot of energy goes into driving practitioner efficiency and making patient data easier for clinicians to access. But is enough focus being put on security and protecting patient data?
News headlines indicate the answer is a resounding no. There have been a slew of notable healthcare breaches in recent years.
Two-Factor Authentication (2FA) Explained: Smart Cards
Smart cards are cards or cryptographic USB tokens that are used for a number of authentication purposes, including physical access (buildings, rooms), computer and network access, and some secure remote access solutions (virtual private networks (VPN), portals).
Two-Factor Authentication (2FA) Explained: One Time Password Hard Tokens
One time passwords (OTPs) are a popular choice for organizations looking to increase their security posture with two-factor authentication. As a refresher, OTPs are unique passwords that are only valid for a single login session and a defined period of time.
Two-Factor Authentication (2FA) Explained: One Time Password Soft Tokens
In today’s dynamic business environment, organizations are putting more and more pressure on users to increase productivity without sacrificing security. However, a company’s infrastructure needs to be nimble enough to meet these needs without negatively affecting user experience.
The Zero Trust Model - What It is and Why It Starts with Identity
The digital transformation has significantly increased risk exposure for enterprises. With users operating a variety of devices from a variety of locations, there is a greater attack surface with less IT oversight and control.
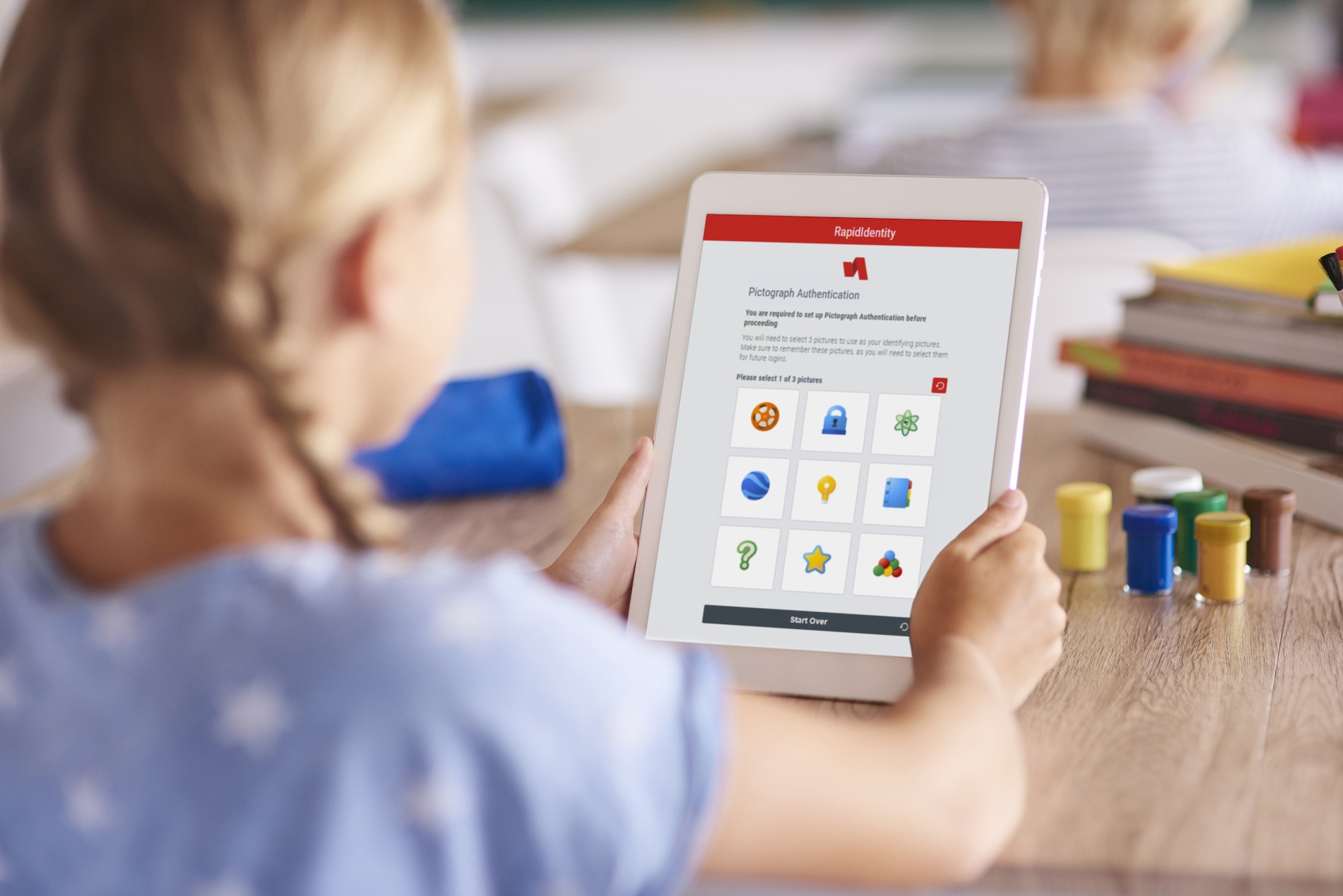
Alternative Authentication for Students, Part 2 - Pictograph Authentication
Technology in the classroom creates usability issues for very young students in pre-k, kindergarten, and first grade, as well as special education students. For many of these students, remembering and typing even simple usernames and traditional passwords is a struggle.
Alternative Authentication for Students, Part 1 - QR Code Badges
Schools are integrating technology and cloud resources into the classroom with ever-growing frequency. Overall education technology spending is expected to reach $19 billion by 2019 on a global scale. It’s easy to see why: Technology in the classroom has the ability to increase collaboration and productivity, create a more personalized learning experience, and enable teachers to distribute assignments and provide real-time feedback.
Meeting Compliance Requirements - What Your Organization Should Know
Let’s be real. Attackers are growing more and more emboldened by the day. As their tools become so simple that even “script kiddies” can use them to wreak havoc on unsuspecting targets, governing bodies are putting added emphasis on tighter regulatory compliance.
current_page_num+2: 5 -