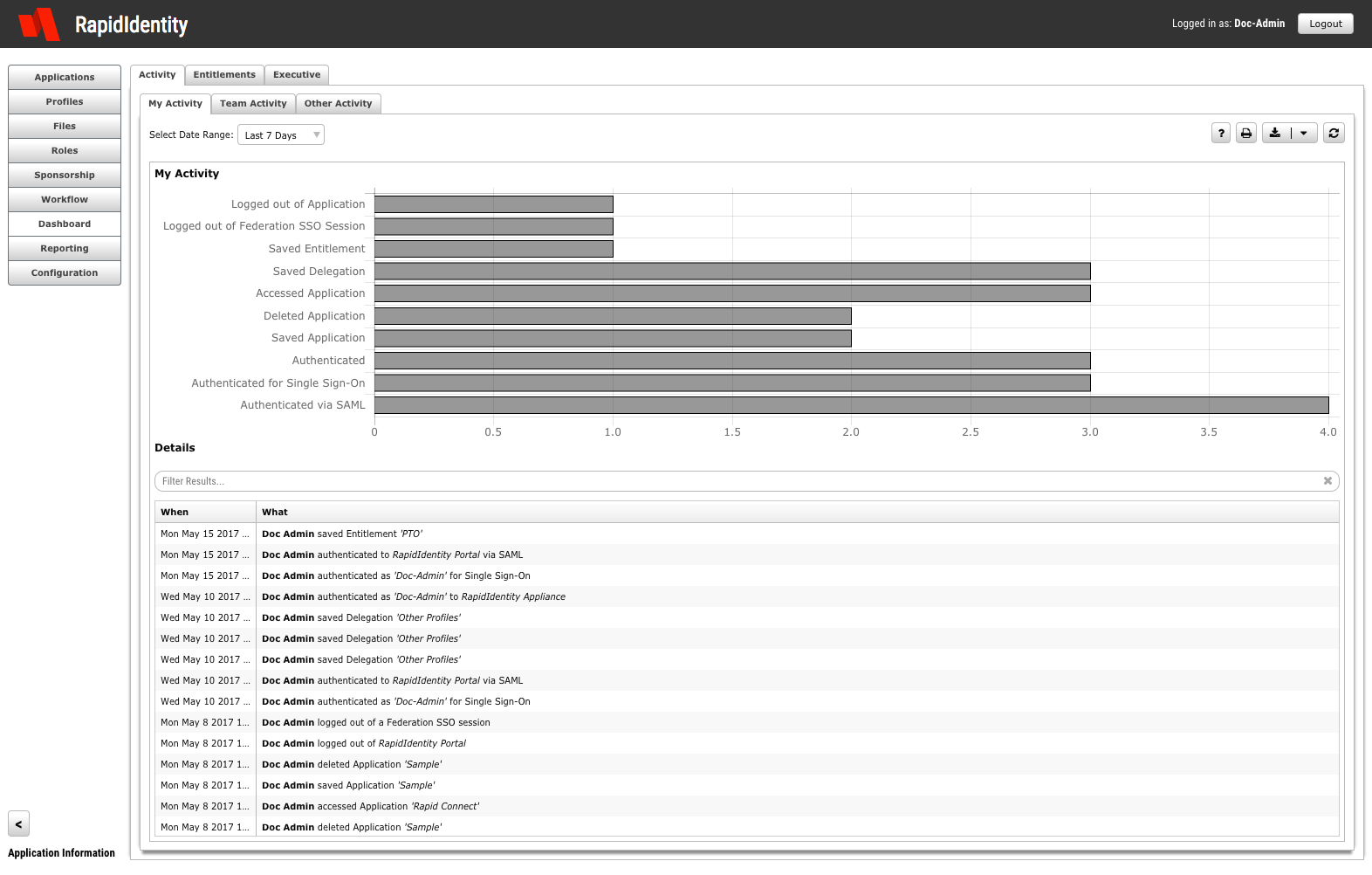
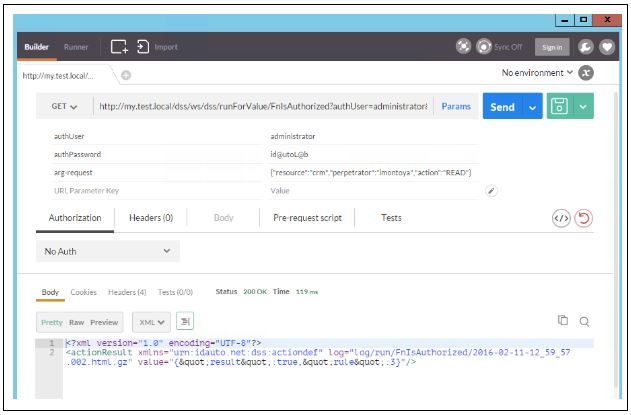
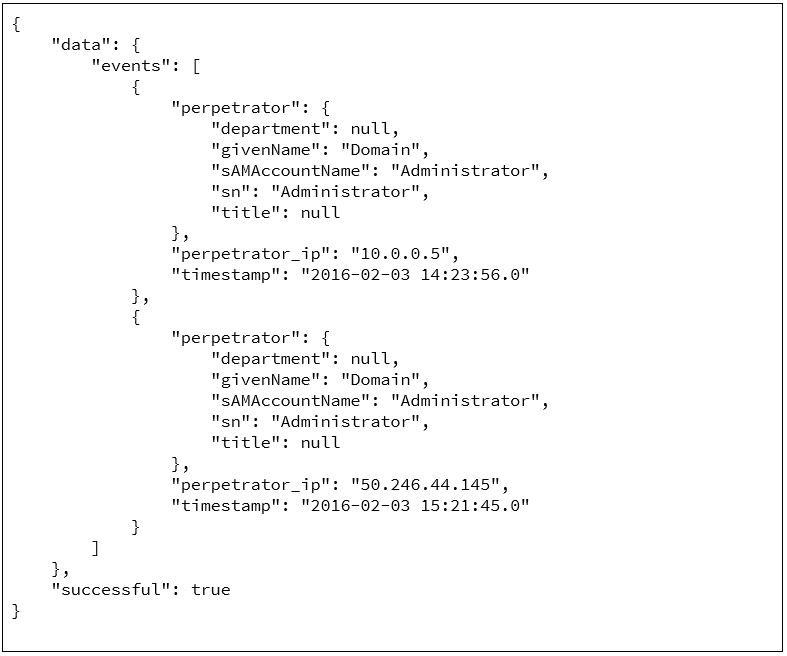
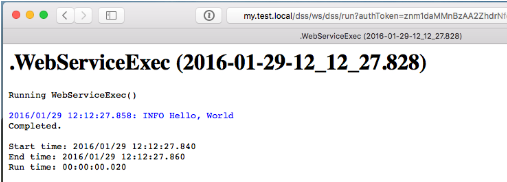
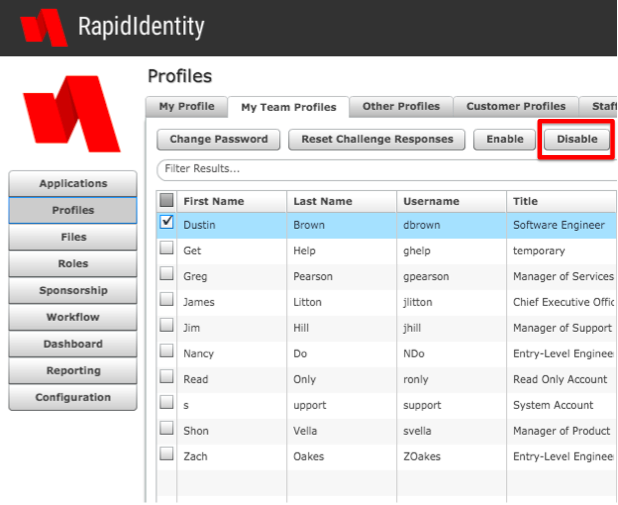
This blog series will focus on reporting with RapidIdentity. Reporting performed within RapidIdentity provides a streamlined approach to obtaining meaningful identity and access management (IAM) data that helps you understand events in a contextual framework and facilitates sensible decision-making. This data can be centered on particular users, groups, or other events within an organization.
Identity Automation Blog
Blog Categories
- Cybersecurity (134)
- Company News (101)
- K-12 Education (80)
- RapidIdentity (71)
- Multi-Factor Authentication (69)
- Higher Education (44)
- Identity Governance (43)
- Identity Lifecycle Management (32)
- Single Sign-On (32)
- Healthcare (29)
- Access Management (19)
- Government & Public Sector (5)
- Identity Automation Pathfinder (1)
Recent Posts by Troy Moreland
Building Web Services with RapidConnect Part 3: Building an Authorization Engine Example
In Part I of our “Building Web Services with RapidConnect” series, I described how to create a simple Web Service using RapidConnect. To summarize, any RapidConnect action set results in having a new Web Service API method. The primary benefit is that users are limited only by imagination and available data to build powerful Web Services to use.
I then discussed inBuilding Web Services with RapidConnect Part 2: Virtual Directory Middleware Example
In Part I of our “Building Web Services with RapidConnect” series, I described how to create a simple Web Service using RapidConnect. To summarize, any RapidConnect action set results in having a new Web Service API method. The primary benefit is that as a user, you are limited only by imagination and available data in building powerful Web Services for your own use.
Introducing the RapidIdentity Technical Blog Series
Our Technical Support and Product teams are often asked for advice and best practices regarding various technical subjects pertaining to our RapidIdentity software. Over the years, we’ve noticed that certain topics have a habit of popping up more than others. We knew that putting together step-by-step resources on these common topics would not only be educational for our customers, but would also enable them to explore these topics at their own pace.
Building Web Services with RapidConnect Part 1: The Basics
One of the great features of RapidConnect is the flexibility to execute action sets. There are three methods for running your action sets:
Interop 2016 Recap: Biometric Authentication and MFA
Earlier this month, I attended the 2016 Interop Conference in Las Vegas. While I had many discussions with attendees on a variety of identity and access security topics, I was surprised by the number of questions about biometrics and multi-factor authentication (MFA). The majority of people asking these questions were interested in better understanding if and how biometrics should be used as part of their authentication process. Since this topic came up so often at Interop, I’m guessing a lot of you have similar questions. So, I thought it would be helpful to provide some additional biometrics and our point our view on them.
RapidIdentity Quick Tip: Ensure Immediate De-Provisioning Through Delegation
We’ve previously discussed the merits of automating the de-provisioning process. But even when automated, sometimes it can still take HR weeks to initiate the off-boarding process of a terminated employee due to alignment with their organizational payroll cycles. From a security perspective, allowing terminated employees to continue to access organization systems for weeks, days or even hours can present significant security risks.
Efficient De-Provisioning: Automation and Other Considerations
Organizations are typically very committed to removing an ex-employee from payroll systems when their employment has ended. No company wants to accidentally give money away to someone who no longer works there. Yet, we rarely see the same efficiency when it comes to de-provisioning that ex-employee from network systems, applications, and all other IT resources. Orphaned accounts can go unnoticed for weeks, months, and sometimes even years.
Three Tips for a More Secure 2FA Program
Last month I read an article reporting that researchers found two-factor authentication to be insecure and vulnerable to hacks. My initial reaction was skepticism, since it wasn’t recommending a more secure alternative like multi-factor authentication, but instead simply stating 2FA isn’t secure.
The Password is Dead and Other 2016 Security Predictions
You could say 2015 was a house of horrors when it came to security breaches -- from high profile corporate hacks, stolen identities of 4 million federal employees, to a database breach exposing the names, genders, and birthdays of more than 200,000 kids.
current_page_num+2: 3 -