
Multi factor Authentication (MFA) is an extremely hot topic among enterprises, education organizations, and consumers alike. Almost daily, we hear about a data breach being discovered in the news. Often, the response to such an intrusion is for the impacted users to change their passwords and enable some type of multi factor authentication on their accounts.
MFA tends to be cited as the most common fix (or augmentation) for the shortcomings of passwords or just as a general alternative to passwords altogether. While there is a lot of truth to MFA providing additional security controls and protection, there are also many other things to consider.
Our three part MFA 101 series explores the breadth and depth of multi factor authentication, examining its benefits and challenges, while providing guidance on when and where to use it. This first part of the series gives a refresher on the basics of multi factor authentication, including commonly used terms for multi factor authentication and examples factor types.
Authentication
Let’s start with the basics. Before we can discuss what MFA is, we need to understand basic authentication. User authentication is a process used to prove that a person is who they claim to be. There are two steps in the authentication process: identification and verification.
During the identification step, a user presents the claimed identifier to the identity system or application. The most common identifier used is the standard username (e.g. jdoe).
The verification step is where the user must prove that they are who they say they are. This is done by providing or generating information that verifies the binding between the information and the identifier. The most common method used for verification is the standard password (e.g. MySecretPassword_123!).
So, What is Multi factor Authentication?
NIST SP 800-63-3 DRAFT defines MFA as a characteristic of an authentication system or an authenticator that requires more than one authentication factor for successful authentication. MFA can be performed using a single authenticator that provides more than one factor or by a combination of authenticators that provide different factors.
The three authentication factors are:
- Something you know (e.g. password)
- Something you have (e.g. token)
- Something you are (e.g. fingerprint)
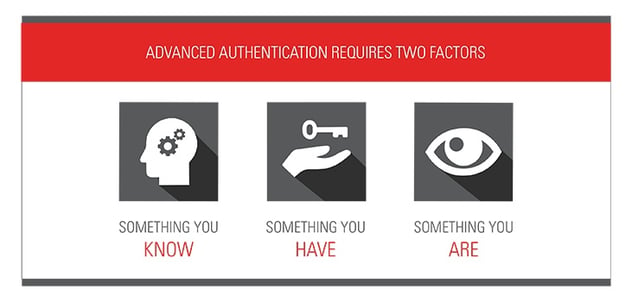
With MFA, the key requirement is using more than one of the factors listed above during the authentication process. For example, when authenticating to an application, a user identifies him or herself with username, then is prompted for a password and an SMS one time passcode on a mobile phone. The password is something the person knows and the SMS passcode is something the person has (via the phone).
It is also noteworthy that other types of information, such as location, time, or device information, may be used by IAM systems during the authentication process. This information can be used as input criteria for policy decisions or risk level, but are not considered a type of authentication factor.
Different Terminology and Factor Types
Depending on what system or application you are using, MFA has different terminology used to describe it and the factors used for verification. Between the many security organizations and application providers, there are a wide variety of names for MFA. So, we want to cover a few that are more commonly used. The key point here is that MFA has many variations on what it is called, but the concepts are all roughly the same.
The table below shows the common names used to describe MFA and some popular applications or organizations that utilize that specific terminology.
| Step-Up Authentication | AuthN with username + password to get access to application but then later prompted for additional AuthN when attempting to access more sensitive data in the application. |
| Advanced Authentication | FBI Criminal Justice Information Services (CJIS) |
| Multi factor Authentication | Amazon AWS, Microsoft Azure, Rackspace, NC DIT |
| 2-Step Verification | Google, LinkedIn, Facebook, Apple, Microsoft, Amazon |
| Two Factor Authentication (2FA) | NCSU, Facebook |
| Login Verification |
In addition, the actual “factors” used to perform the identification and/or verification step can vary as well. The chart below lists of some common factor types used during authentication.
Conclusion
Given the breadth of terminology and factor types, multi factor authentication can seem like an overwhelming topic. Fortunately, by covering how authentication works and common terminology and factor types, you are well on your way to understanding of the basics of what multi factor authentication is.
Now, it’s important that you determine your organization’s unique requirements and motivations for implementing multi factor authentication, since these will vary from organization to organization. Stay tuned, in part two of our MFA 101 series where we will discuss WHY organizations implement multi factor authentication and how this impacts the challenges and benefits of an MFA solution.


Comments