More and more, organizations are looking for cost-effective alternatives to traditional passwords that increase security without affecting usability. Many people believe that push notification authentication, a newer mobile-based authentication method, could be the answer.
With push authentication, access requests are sent via out-of-band notifications to an associated mobile device that a user then approves or denies. Although only 10 percent of enterprises with mobile authentication in place use push notifications today, Gartner predicts that number will jump to 50 percent by 2020.
So, what’s driving this adoption?
Let’s take a closer look at how push authentication works and its benefits, as well as potential drawbacks organizations should consider when evaluating it as an authentication option.
How Push Notification Authentication Works
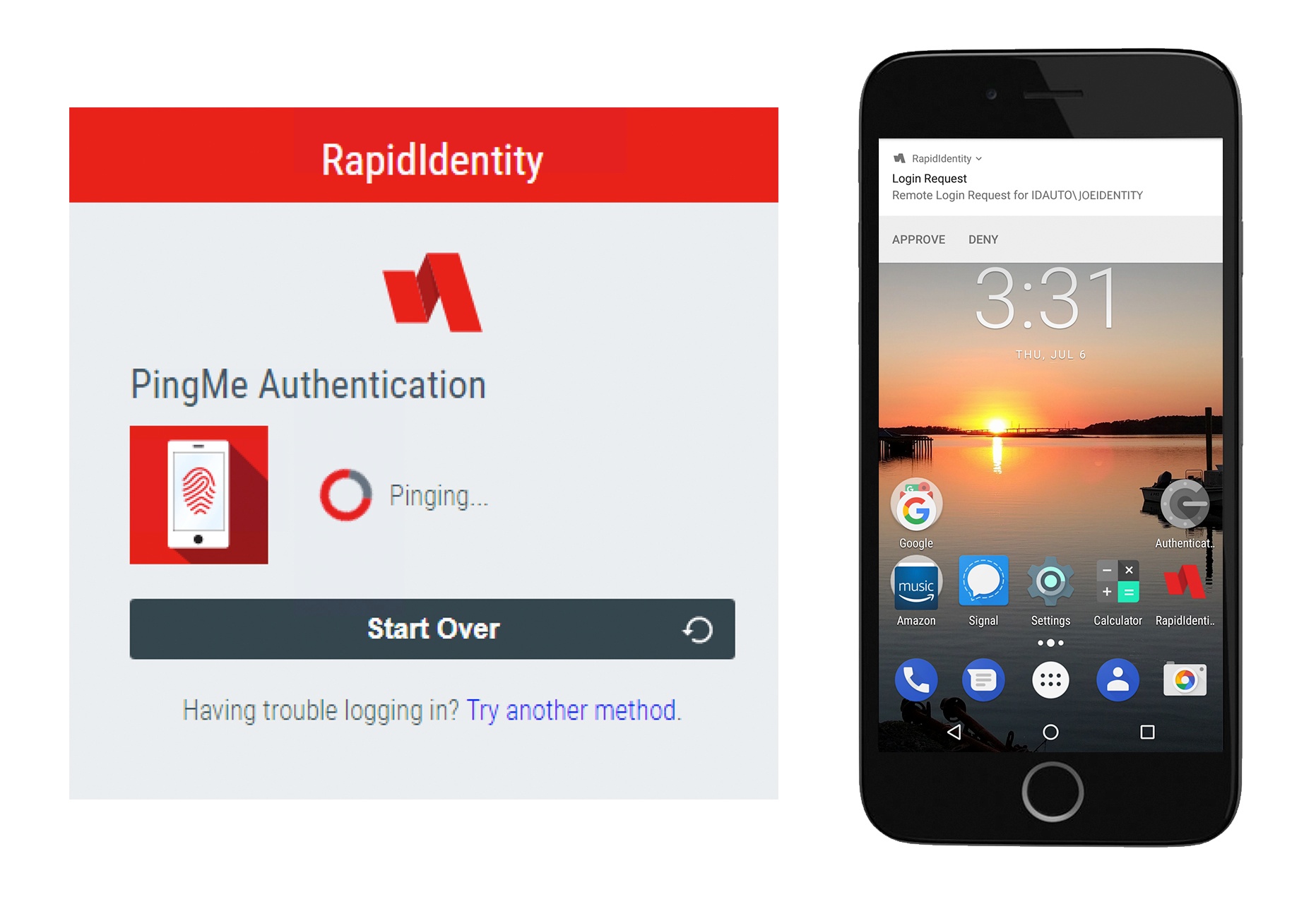
To enable push authentication, a user downloads the push authentication app, such as RapidIdentity PingMe, to his or her smartphone and enrolls his or her user account. This associates the user’s smartphone to the server.
Then, on the web page login, the user enters his or her username and clicks the login prompt to send a push notification in addition to or in place of entering a password. Next, the server sends a push notification to the user’s registered smartphone.
When the user receives the push authentication request on the smartphone, there is a prompt to approve or deny the request with a simple tap. When the user approves the request, the server receives that request and proceeds with logging the user into the web application.
Denying the request not only prevents authentication, but there’s also an option to alert an admin or other relevant party that the request for authentication was denied, so appropriate action can be taken.
Benefits
Password Replacement
When push authentication is used in lieu of a password, it eliminates this less secure authentication method. As such, users aren’t at risk of falling prey to phishing, man-in-the-middle, and brute force attacks. Moreover, this eliminates the use of bad password habits, such as writing passwords down, repeating passwords, or using simple or common passwords.
Another benefit of getting rid of passwords is freeing up your help desk from dealing with password reset requests. Gartner estimates that 20-50 percent of all help desk calls are for password resets, and Forrester researchers have calculated the cost of a single password reset to be $70, so the time and soft cost savings can add up quickly.
User Convenience
Push authentication is fast and easy to use—all users do is approve the push notification with the tap of a finger to immediately gain access. There’s no typing, copying a code, or having to remember anything. Plus, many users already have smartphones and are comfortable with using mobile technologies.
Out-of-Band
It’s hard to ignore the security benefits of push notifications. These out-of-band communications cannot be intercepted at the point of password entry. Communications are encrypted from end to end between the application and a secured authentication service.
More Secure
In addition to being out-of-band, push authentication offers a number of other security advantages. Unlike SMS one time passwords, where a notification containing a code may be visible on a locked phone screen, push notifications don’t contain a code, and the device must be unlocked to approve a notification. Even if a user’s smartphone falls into the wrong hands, the device’s PIN code, FaceID, or TouchID protects against unauthorized access.
Furthermore, notifications are sent in real time, so if there is a fraudulent access request, a user is empowered to deny the request and immediately take action, unlike reactive fraud alerts that only notify a victim after the fact.
Another crucial consideration is that push authentication is recommended by the National Institute of Standards and Technology (NIST). The agency’s guidelines state, “If out of band verification is to be made using a secure application (e.g., on a smartphone), the verifier MAY send a push notification to that device.”
Frictionless MFA
Push authentication makes it easier than ever to enable multi-factor authentication (MFA). When the user combines push authentication with the locking function of his or her smartphone, this establishes a viable form of MFA. The user’s registered phone acts as the first authentication factor (something you have), and the phone’s Touch ID, FaceID (something you are), or PIN (something you know) is the second.
This frictionless MFA can significantly reduce the “security hate factor” among your users. Security hate factor is a term for the usability headaches and bad feelings that occur when newly implemented security policies and technologies cause added disruption and inconvenience without adding noticeable user benefits.
Low Cost and Ease of Administration
Push authentication leverages users’ existing smartphones, making it a lower cost choice for security that doesn’t have any hardware that must be managed.
Ease of administration is another boon. Users can download and install the app on their smartphones without the assistance of IT, and the app updates automatically. Users can even register multiple devices.
Drawbacks
Security Vulnerabilities
Although push authentication is more secure than other authentication methods, security risks still exist. For starters, it is possible for users to accidentally approve a fraudulent request.It’s easy to get in the habit of clicking “approve” when receiving notifications. Studies have shown that there is a dramatic drop in attention when a user is shown even just two security warnings in a short period of time.
However, this shortcoming can be overcome by including a push notification request number in push notifications. The phone will say, “Please approve request ECG2 on the local system,” and the user has to match the request number on his or her phone to approve the request.
Moreover, devices on which the software is installed are not completely isolated from external influences. Smartphones are vulnerable to attacks and viruses, like any device with an operating system. This is especially true for Android devices.
Requires a Smartphone
Although many users feel comfortable using their mobile devices for work purposes, some may not want to or may not have a suitable device on which to receive push notifications (that is to say, they don’t have a smartphone). In addition, phones have to be recharged daily, so if your smartphone battery dies, you can’t authenticate via this method.
Requires Internet Connection
Unlike some other authentication methods, such as hard and soft OTPs, push authentication requires an internet connection, so in scenarios where a user doesn’t have access to the internet, push notifications aren’t an authentication option.
Devices Can Be Lost or Stolen
One of the disadvantages of push authentication is that devices can be lost or stolen. That being said, all is not lost. If this happens, it’s just a matter of reprovisioning the push authentication app on the user’s new mobile device. Additionally, if the device is stolen, its PIN, TouchID, FaceID still prevents unauthorized access.
Push Notification Authentication: Is It the Right Choice for You?
Push authentication adoption is rapidly growing because it offers a low-cost, easy-to-use, and secure replacement for traditional passwords. So, is push authentication right for your organization? That depends on your organization’s needs, but for many, it’s a way to implement secure MFA without negatively impacting user experience.


Comments