In today’s digital world, information security has quickly become one of the foremost areas of concern for individuals and businesses alike. Particularly in the business realm, government regulations, such as the Payment Card Industry Data Security Standard (PCI DSS) and the Health Insurance Portability and Accountability Act (HIPAA), require close security auditing and penetration testing in order to ensure consumer, patient, and business data are handled securely (i.e. storage, retrieval, transmission, and authorized access).
This blog post demonstrates using RapidIdentity Connect to automate vulnerability scanning using the free, open source scanner, OpenVAS.
Scenario
A (fictitious) customer, the Foundation for Fantastic Fundraising (i.e. 3F) runs a data center containing 1000 Linux servers. 3F solicits public funds for a variety of nonprofit organizations, dealing primarily with children’s charities and retirement homes.
3F's (also fictitious) Chief Information Security Officer (CISO), Ima Stickler, was recently hired to address many of the growing company’s security concerns, particularly their lack of IT security auditing for their Linux server farm. Mr. Stickler decided to implement a vulnerability assessment tool in order to scan 3F’s hosts to help ensure that any security holes would be found and addressed, and he chose OpenVAS as the tool of choice.
Author’s note: OpenVAS is one of MANY recognized vulnerability scanners in the security industry. For this example, it was chosen for its ease of command-line configuration.
Ima’s security team implemented OpenVAS, but soon discovered that their scans were inefficient, due to scanning unnecessary ports and services, as well as scanning entire subnets when they ultimately wanted to limit specific scans to certain subsets of servers and only against their listening ports/services. Realizing the need for efficient automation, they approached Identity Automation to see if our experts could help to engineer a solution.
Solution
This solution has three main parts: a functional OpenVAS server; using the RapidIdentity Connect Command Line Interface (CLI) adapter to configure OpenVAS; and using actions to save, zip, and email actions to gathering the final reports. All actions used in this solution will appear, in their entirety, in the Files area at the end of this post.
The solution begins with a simple action (PrimaryHosts) to define the scan targets. Next, it iterates through the defined hosts and gets their “listening” ports, calling GetLinuxListenerPorts. Once both the hosts and their listener ports are enumerated, LinuxOpenVASScan configures and executes the proper vulnerability scans for each host.
Finally, I’ll provide GetOpenVASReports, which can be run after all scans have completed (but before the next scheduled scan cycle - to be explained later) within OpenVAS to retrieve and if desired, email the reports to the proper support / security / management personnel.
To start, ensure that an OpenVAS server is set up and functional. For this example, I set up OpenVAS 9 on an Ubuntu Linux 14.04 host. While I won’t cover the installation of the Ubuntu Linux OS, I followed the OpenVAS instructions from launchpad to get OpenVAS operational on the host.
Additional packages are required on the OpenVAS server to export OpenVAS reports as PDF documents. To install those libraries on the host, run this command:
sudo apt-get install textlive-latex-base textlive-latex-extra -y
Once OpenVAS and the textlive libraries are installed, these three services must be running also.
[ + ] openvas-gsa
[ + ] openvas-manager
[ + ] openvas-scanner
To check their status, run:
sudo service --status-all
If the services are running, the plus sign will be present, as shown above. If any of these three services are not running, each service can be started using this command:
sudo service name start
In this command, the name is openvas-gsa, openvas-manager, or openvas-scanner.
Once the services are running, it should be possible to manually log in to the Greenbone Security Assistant console. To access this console, open a browser tab and type https://ubuntuhost:4000, where “ubuntuhost” is your host using the default username:password of admin:admin; of course, this username and password can be changed later.
Once authenticated to the console, create Targets, Port Definitions, and Tasks by hand, then run them (outside of the scope of this blog post), if you want to confirm all is working before proceeding.
Now that the services are running and the console is accessible, create a custom scan and name it “IDAutoScan”. As a side note, I created IDAutoScan in OpenVAS with vulnerabilities relevant to our Linux hosts, which had AWS, SuSE, RedHat / CentOS, and application / network vulnerability sets included. IDAutoScan will be used as an input value for the scanType property in the first action, PrimaryHosts.
With these steps completed, RapidIdentity Connect can now be used effectively. Let’s start with the PrimaryHosts action.
The purpose of the PrimaryHosts action is to control the process, from beginning to end, by defining scan targets and passing them into the other actions. For this example, we’ve defined two hard-coded hosts, whereas the reader could have the action accept input, read hosts from file, or use some other, more “dynamic” method for generating the hosts list. The entire PrimaryHosts action is below.
hosts = createRecord()
setRecordFieldValue(hosts, "192.168.120.235", "192.168.120.235")
setRecordFieldValue(hosts, "192.168.120.236", "192.168.120.236")
portsToScan = GetLinuxListenerPorts(hosts)
LinuxOpenVASScan(portsToScan, hosts, scanType)
Now that the hosts record is defined and the target hosts have been added to it, PrimaryHosts passes the record into the GetLinuxListenerPorts action. GetLinuxListenerPorts accepts the hosts record as input and iterates through the field names as ip addresses. This action establishes an SSH connection to each IP address, checks what listening ports the IP address has, and appends any new ports that are discovered to a master array of ports if they’re not already present in the array. The action then returns the entire ports array to PrimaryHosts to be used subsequently as portsToScan when calling into the final action, LinuxOpenVASScan.
ports = createArray()
hosts = getRecordFieldNames(hostRecords)
forEach(host, hosts) {
linuxCLI = openRemoteCLI(host, "root",)
netstatCommand = runRemoteCLICommand(linuxCLI, "netstat -antp | grep LISTEN | awk '{print $4}' | sed 's/.*://' | sed '/^[0-9]/!d'")
listeningPorts = splitString(netstatCommand['output'], "\n")
forEach(listeningPort, listeningPorts) {
portFound = arrayContains(ports, listeningPort)
if(!portFound) {
appendArrayItem(ports, listeningPort)
} else {
}
}
close(linuxCLI)
}
sortArray(ports)
removedBlankPort = removeArrayItem(ports, 0)
return(ports)
Moving forward, with the defined record (hosts) and array (ports), the action progresses into LinuxOpenVASScan. This action accepts three input properties: ports, hosts, and scanType (recall that scanType was defined earlier during the OpenVAS setup process). To help keep track of the flow, we’ve defined an actionInfo section, which contains the order of operation for what this action does.
actionInfo: {
# 1 - This action accepts a list of ports, a list of hosts (as a record of records) and a scanType (as defined within openVAS).
# 2 - It then creates ports string to be used in the openVas scan.
# 3 - Next it gets the config ID from openVAS for the selected scanType.
# 4a - It then iterates through the hosts that were passed in, deleting existing Tasks, Targets and port ranges, so they can be redefined.
# 4b - This was necessary, as otherwise, port changes cannot take effect if the target and port list are already in use.
# 5 - For each host, it then creates a new Target with the defined ports list
# 6 - Next, a task is created to scan the target, with the input scan type
# 7 - It then runs the scan task for the host and scanType.
}
Continuing on, the action opens a CLI connection to the OpenVAS host.
establishOpenVASConnection: {
# Open CLI to openVAS server
openVASCLI = openRemoteCLI("192.168.120.51", "infosec",)
}
Next, the action compiles a port string to be passed in a subsequent command.
getApplianceTCPPorts: {
# Build port string
{
portString = "T:"
forEach(port, ports) {
portString = portString + port + ","
}
lengthPortString = stringLength(portString)
portString = subString(portString, 0, lengthPortString - 1)
}
}
OpenVAS is queried, to retrieve the proper configuration information for our scanType and the action prepares the hosts list for the remainder of the action.
getOpenVASConfig: {
getConfigIDString = "omp -u admin -w -g | grep \"" + scanType + "\" | cut -d \" \" -f 1"
configID = runRemoteCLICommand(openVASCLI, getConfigIDString)
configID = splitString(configID['output'], "\n")
configID = configID[0]
}
# Determine appliances to scan
appliances = getRecordFieldNames(hosts)
Here is where the process gets a little more complicated. Because OpenVAS scans are typically hard-coded and specific configuration items rely on others, many of the settings for a scan cannot be modified while they’re ‘in use’ by a connected item.
For example, defined port ranges cannot be changed while a host entry has them assigned to it. This is why, as mentioned in the beginning of our Solution section, reports need to be gathered after a vulnerability scan pass has run completely, but before another scheduled run, in that if hosts are deleted, corresponding reports for those hosts are deleted as well.
At this point, the action iterates through the hosts, deleting prior configuration items that pertain to each host.
forEach(appliance, appliances) {
deleteOpenVASTasks: {
# Can't modify targets if assigned to TASK so need to whack existing tasks for target if they exist
{
taskQueryString = "omp -u admin -w --xml=''"
existingTasks = runRemoteCLICommand(openVASCLI, taskQueryString)
existingTasks = splitString(existingTasks['output'], "")
existingTasks = splitString(existingTasks[1], "")
existingTasks = splitString(existingTasks[0], "")
removed = removeLastArrayItem(existingTasks)
forEach(existingTask, existingTasks) {
taskExists = stringContains(existingTask, scanType + " on " + appliance)
if(taskExists) {
taskExistArray = splitString(existingTask, "\"")
taskID = taskExistArray[1]
deleteTaskString = "omp -u admin -w --xml=''"
deletedTask = runRemoteCLICommand(openVASCLI, deleteTaskString)
} else {
}
}
}
}
deleteOpenVASTarget: (false) {
# Delete target
{
queryTargetIDString = "omp -u admin -w -T | grep " + appliance
targetID = runRemoteCLICommand(openVASCLI, queryTargetIDString)
targetExists = stringContains(targetID['output'], appliance)
# Get Target ID
{
getTargetIDString = "omp -u admin -w -T | grep " + appliance + " | cut -d \" \" -f 1"
targetID = runRemoteCLICommand(openVASCLI, getTargetIDString)
targetID = targetID['output']
targetID = stringReplaceAll(targetID, "\n", "")
}
targetDeleteString = "omp -u admin -w --xml=''"
targetDeleted = runRemoteCLICommand(openVASCLI, targetDeleteString)
}
}
deleteOpenVASPortsList: {
# If port list exists, delete it
{
getOpenVASPortsListString = "omp -u admin -w --xml=''"
fullPortsLists = runRemoteCLICommand(openVASCLI, getOpenVASPortsListString)
portsListExists = stringContains(fullPortsLists['output'], appliance)
if(portsListExists) {
portLists = splitString(fullPortsLists['output'], " --xml=''"
deletePortsList = runRemoteCLICommand(openVASCLI, deleteOpenVASPortsListString)
} else {
}
}
} else {
}
}
}
}
With the previous hosts and tasks deleted, the hosts are iterated again and new hosts and tasks are created in OpenVAS.
forEach(appliance, appliances) {
createOpenVASTarget: {
createTargetString = "omp -u admin -w --xml='" + appliance + "" + appliance + "" + portString + "'"
createdTarget = runRemoteCLICommand(openVASCLI, createTargetString)
}
createOpenVASTask: {
# Get Target ID
{
getTargetIDString = "omp -u admin -w -T | grep " + appliance + " | cut -d \" \" -f 1"
targetID = runRemoteCLICommand(openVASCLI, getTargetIDString)
targetID = targetID['output']
targetID = stringReplaceAll(targetID, "\n", "")
}
# Create task
{
taskCreateString = "omp -u admin -w --xml='" + scanType + " on " + appliance + "" + scanType + " on " + appliance + "'"
createdTask = runRemoteCLICommand(openVASCLI, taskCreateString)
}
}
The action retrieves the task ID’s from OpenVAS and then runs each task.
runOpenVASTask: {
# Get Task ID
{
existingTasks = runRemoteCLICommand(openVASCLI, taskQueryString)
existingTasks = splitString(existingTasks['output'], "")
existingTasks = splitString(existingTasks[1], "")
existingTasks = splitString(existingTasks[0], "")
removed = removeLastArrayItem(existingTasks)
forEach(existingTask, existingTasks) {
taskExists = stringContains(existingTask, scanType + " on " + appliance)
if(taskExists) {
taskExistArray = splitString(existingTask, "\"")
taskID = taskExistArray[1]
} else {
}
}
}
# Run Task
{
runTaskString = "omp -u admin -w --xml=''"
taskRun = runRemoteCLICommand(openVASCLI, runTaskString)
}
}
}
Finally, the CLI connection to the OpenVAS server is closed.
closeOpenVASConnection: {
# Close CLI to openVAS server
close(openVASCLI)
}
With the actions in place, go ahead and run your first scan to change the IP/host information in the original PrimaryHosts action, as needed, to match your environment.
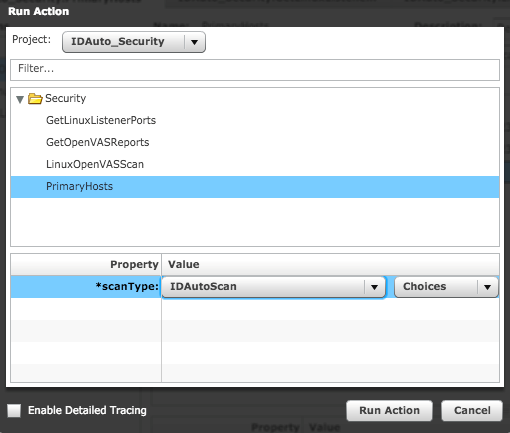
At this point, OpenVAS is running one or more vulnerability scans. For the purposes of this blog post, there were two hard-coded hosts, so two scans are running. The RapidIdentity Connect action completes quickly; however, its job was to create configurations and tell OpenVAS to run its scans. Thus, RapidIdentity Connect is now out of the loop. In the browser window with the Greenbone Security Assistant console, the status of running scans can be viewed.
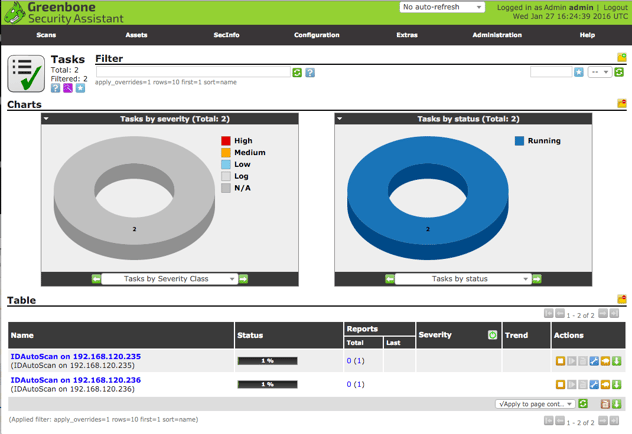
Additionally, you can view the created targets (hosts) with links to their port lists (OpenVAS assigns each host it’s own port list when created from the command line) from within Greenbone Security Assistant as well.
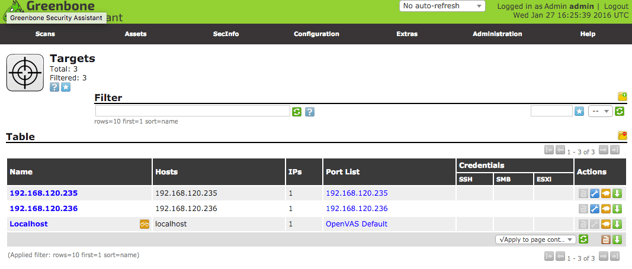
Scan reports can be retrieved from within the Greenbone Security Assistant individually until the next scheduled run of the actions, or they may be retrieved and stored in the RapidIdentity Connect files area.
These same reports can be optionally zipped and emailed to a specific user by running a final action, GetOpenVASReports, which we’ll discuss next. note that only reports for completed scans are retrievable with GetOpenVASReports.
GetOpenVASReports allows administrators to schedule retrieval of all existing host reports that were created by the actions, above. It accepts one optional input parameter, email, to provide the ability to not only store, but email a copy of the reports to a specified user. This action begins with retrieving global variables, specifying a PDF report format, opening a CLI connection to the OpenVAS server, and setting a date variable to be used in the folder and filename creation.
# Get proper report format string
{
formatsString = runRemoteCLICommand(openVASCli, "omp -u admin -w --xml=''")
formats = splitString(formatsString['output'], "report_format ")
forEach(format, formats) {
if(foundFormat) {
continue()
} else {
}
foundFormat = stringContains(format, reportformat, true)
if(foundFormat) {
formatSplit = splitString(format, "\"")
formatID = formatSplit[1]
log(reportformat + " : has formatID of " + formatID, "\"green\"")
} else {
}
}
if(!foundFormat) {
log("Could not find a defined report format named: " + reportformat, "red")
log("Exiting", "red")
return()
} else {
}
}
Subsequently, the current (existing) report IDs are retrieved.
# Retrieve report ID's
{
reportsIDsString = runRemoteCLICommand(openVASCli, "omp -u admin -w --xml=''")
reports = splitString(reportsIDsString['output'], "report id=\"")
removedInvalid = removeArrayItem(reports, 0)
reportIDs = createRecord()
forEach(report, reports) {
report = splitString(report, "\"")
setRecordFieldValue(reportIDs, report[0], report[0])
}
repIDs = getRecordFieldNames(reportIDs)
}
With the report IDs in hand, the actual report data is queried and stored in RapidIdentity Connect’s files module.
# Get reports
{
forEach(repID, repIDs) {
getReportString = "omp -u admin -w --xml=''"
reportString = runRemoteCLICommand(openVASCli, getReportString)
hostString = splitString(reportString['output'], "IDAutoScan on ")
hostString = splitString(hostString[1], "")
hostIP = hostString[0]
reportString = splitString(reportString['output'], "application/pdf\">")
reportString = splitString(reportString[1], "")
# reportData = decodeBase64ToString(reportString[0])
reportData = decodeBase64ToBytes(reportString[0])
# log(reportData)
logDirFound = isDirectory("/reports/OpenVAS")
if(!logDirFound) {
createdLogDir = createDirectory("/reports/OpenVAS")
} else {
}
dateDirFound = isDirectory("/reports/OpenVAS/" + runDate)
if(!dateDirFound) {
createdDateDir = createDirectory("/reports/OpenVAS/" + runDate)
} else {
}
saveToFile("/reports/OpenVAS/" + runDate + "/" + runDate + "-" + hostIP + "-OpenVASScan.pdf", reportData)
}
}
Finally, if the email input property was set to “yes”, the action creates a zip file of the current fileset, emails the zip file to the address inside the action, deletes the temporary zip file, and closes the CLI connection with the OpenVAS Server.
# If email is requested - zip, email, then delete zip file
{
if(email == "yes") {
filesZipped = zipFile("/reports/OpenVAS/" + runDate, "/reports/" + runDate + "-OpenVAS.zip")
mailSent = sendEmail(Global.smtpServer, "587", "STARTTLS", Global.smtpAccount,, Global.smtpSecuritySender, Global.smtpSecurityRecipient, "OpenVAS Reports - " + runDate, "Attached, please find a zip file of the OpenVAS reports from the " + runDate + " run.", "/reports/" + runDate + "-OpenVAS.zip")
} else {
}
fileDeleted = deleteFile("/reports/" + runDate + "-OpenVAS.zip")
}
# Close Remote OpenVAS CLI
close(openVASCli)
An individual scan report from OpenVAS will take the following form.
The output report concludes the integration of RapidIdentity Connect with OpenVAS in the context of vulnerability scans. The final two blog posts of this series, Managing Infrastructure with RapidIdentity, will focus on integrating RapidIdentity with Amazon Web Services. Stay tuned!
Files
PrimaryHosts (Input Properties: scanType:IDAutoScan:Full and fast)
Note: scanType is a specific value that was configured within OpenVAS in our blog post, or it can also be set to “Full and fast” or another predefined OpenVAS scan configuration.
hosts = createRecord()
setRecordFieldValue(hosts, "192.168.120.235", "192.168.120.235")
setRecordFieldValue(hosts, "192.168.120.236", "192.168.120.236")
portsToScan = GetLinuxListenerPorts(hosts)
LinuxOpenVASScan(portsToScan, hosts, scanType)
GetLinuxListenerPorts (Input Properties: hostRecords:object)
ports = createArray()
hosts = getRecordFieldNames(hostRecords)
forEach(host, hosts) {
linuxCLI = openRemoteCLI(host, "root",)
netstatCommand = runRemoteCLICommand(linuxCLI, "netstat -antp | grep LISTEN | awk '{print $4}' | sed 's/.*://' | sed '/^[0-9]/!d'")
listeningPorts = splitString(netstatCommand['output'], "\n")
forEach(listeningPort, listeningPorts) {
portFound = arrayContains(ports, listeningPort)
if(!portFound) {
appendArrayItem(ports, listeningPort)
} else {
}
}
close(linuxCLI)
}
sortArray(ports)
removedBlankPort = removeArrayItem(ports, 0)
return(ports)
LinuxOpenVASScan (Input properties: ports:object, hosts:object, scanType:text)
actionInfo: {
# 1 - This action accepts a list of ports, a list of hosts (as a record of records) and a scanType (as defined within openVAS).
# 2 - It then creates ports string to be used in the openVas scan.
# 3 - Next it gets the config ID from openVAS for the selected scanType.
# 4a - It then iterates through the hosts that were passed in, deleting existing Tasks, Targets and port ranges, so they can be redefined.
# 4b - This was necessary, as otherwise, port changes cannot take effect if the target and port list are already in use.
# 5 - For each host, it then creates a new Target with the defined ports list
# 6 - Next, a task is created to scan the target, with the input scan type
# 7 - It then runs the scan task for the host and scanType.
}
establishOpenVASConnection: {
# Open CLI to openVAS server
openVASCLI = openRemoteCLI("192.168.120.51", "infosec",)
}
getApplianceTCPPorts: {
# Build port string
{
portString = "T:"
forEach(port, ports) {
portString = portString + port + ","
}
lengthPortString = stringLength(portString)
portString = subString(portString, 0, lengthPortString - 1)
}
}
getOpenVASConfig: {
getConfigIDString = "omp -u admin -w -g | grep \"" + scanType + "\" | cut -d \" \" -f 1"
configID = runRemoteCLICommand(openVASCLI, getConfigIDString)
configID = splitString(configID['output'], "\n")
configID = configID[0]
}
# Determine appliances to scan
appliances = getRecordFieldNames(hosts)
forEach(appliance, appliances) {
deleteOpenVASTasks: {
# Can't modify targets if assigned to TASK so need to whack existing tasks for target if they exist
{
taskQueryString = "omp -u admin -w --xml=''"
existingTasks = runRemoteCLICommand(openVASCLI, taskQueryString)
existingTasks = splitString(existingTasks['output'], "")
existingTasks = splitString(existingTasks[1], "")
existingTasks = splitString(existingTasks[0], "")
removed = removeLastArrayItem(existingTasks)
forEach(existingTask, existingTasks) {
taskExists = stringContains(existingTask, scanType + " on " + appliance)
if(taskExists) {
taskExistArray = splitString(existingTask, "\"")
taskID = taskExistArray[1]
deleteTaskString = "omp -u admin -w --xml=''"
deletedTask = runRemoteCLICommand(openVASCLI, deleteTaskString)
} else {
}
}
}
}
deleteOpenVASTarget: (false) {
# Delete target
{
queryTargetIDString = "omp -u admin -w -T | grep " + appliance
targetID = runRemoteCLICommand(openVASCLI, queryTargetIDString)
targetExists = stringContains(targetID['output'], appliance)
# Get Target ID
{
getTargetIDString = "omp -u admin -w -T | grep " + appliance + " | cut -d \" \" -f 1"
targetID = runRemoteCLICommand(openVASCLI, getTargetIDString)
targetID = targetID['output']
targetID = stringReplaceAll(targetID, "\n", "")
}
targetDeleteString = "omp -u admin -w --xml=''"
targetDeleted = runRemoteCLICommand(openVASCLI, targetDeleteString)
}
}
deleteOpenVASPortsList: {
# If port list exists, delete it
{
getOpenVASPortsListString = "omp -u admin -w --xml=''"
fullPortsLists = runRemoteCLICommand(openVASCLI, getOpenVASPortsListString)
portsListExists = stringContains(fullPortsLists['output'], appliance)
if(portsListExists) {
portLists = splitString(fullPortsLists['output'], " --xml=''"
deletePortsList = runRemoteCLICommand(openVASCLI, deleteOpenVASPortsListString)
} else {
}
}
} else {
}
}
}
}
forEach(appliance, appliances) {
createOpenVASTarget: {
createTargetString = "omp -u admin -w --xml='" + appliance + "" + appliance + "" + portString + "'"
createdTarget = runRemoteCLICommand(openVASCLI, createTargetString)
}
createOpenVASTask: {
# Get Target ID
{
getTargetIDString = "omp -u admin -w -T | grep " + appliance + " | cut -d \" \" -f 1"
targetID = runRemoteCLICommand(openVASCLI, getTargetIDString)
targetID = targetID['output']
targetID = stringReplaceAll(targetID, "\n", "")
}
# Create task
{
taskCreateString = "omp -u admin -w --xml='" + scanType + " on " + appliance + "" + scanType + " on " + appliance + "'"
createdTask = runRemoteCLICommand(openVASCLI, taskCreateString)
}
}
runOpenVASTask: {
# Get Task ID
{
existingTasks = runRemoteCLICommand(openVASCLI, taskQueryString)
existingTasks = splitString(existingTasks['output'], "")
existingTasks = splitString(existingTasks[1], "")
existingTasks = splitString(existingTasks[0], "")
removed = removeLastArrayItem(existingTasks)
forEach(existingTask, existingTasks) {
taskExists = stringContains(existingTask, scanType + " on " + appliance)
if(taskExists) {
taskExistArray = splitString(existingTask, "\"")
taskID = taskExistArray[1]
} else {
}
}
}
# Run Task
{
runTaskString = "omp -u admin -w --xml=''"
taskRun = runRemoteCLICommand(openVASCLI, runTaskString)
}
}
}
closeOpenVASConnection: {
# Close CLI to openVAS server
close(openVASCLI)
}
GetOpenVASReports (Input Properties: email?:yes:no)
Globals()
# Set report format
reportformat = "pdf"
# Open Remote OpenVAS CLI
openVASCli = openRemoteCLI("192.168.120.51", "infosec",)
# Set Date variable for directory / filename
{
timestamp = now()
runDate = formatDate(timestamp, "yyyyMMDD")
}
# Get proper report format string
{
formatsString = runRemoteCLICommand(openVASCli, "omp -u admin -w --xml=''")
formats = splitString(formatsString['output'], "report_format ")
forEach(format, formats) {
if(foundFormat) {
continue()
} else {
}
foundFormat = stringContains(format, reportformat, true)
if(foundFormat) {
formatSplit = splitString(format, "\"")
formatID = formatSplit[1]
log(reportformat + " : has formatID of " + formatID, "\"green\"")
} else {
}
}
if(!foundFormat) {
log("Could not find a defined report format named: " + reportformat, "red")
log("Exiting", "red")
return()
} else {
}
}
# Retrieve report ID's
{
reportsIDsString = runRemoteCLICommand(openVASCli, "omp -u admin -w --xml=''")
reports = splitString(reportsIDsString['output'], "report id=\"")
removedInvalid = removeArrayItem(reports, 0)
reportIDs = createRecord()
forEach(report, reports) {
report = splitString(report, "\"")
setRecordFieldValue(reportIDs, report[0], report[0])
}
repIDs = getRecordFieldNames(reportIDs)
}
# Get reports
{
forEach(repID, repIDs) {
getReportString = "omp -u admin -w --xml=''"
reportString = runRemoteCLICommand(openVASCli, getReportString)
hostString = splitString(reportString['output'], "IDAutoScan on ")
hostString = splitString(hostString[1], "")
hostIP = hostString[0]
reportString = splitString(reportString['output'], "application/pdf\">")
reportString = splitString(reportString[1], "")
# reportData = decodeBase64ToString(reportString[0])
reportData = decodeBase64ToBytes(reportString[0])
# log(reportData)
logDirFound = isDirectory("/reports/OpenVAS")
if(!logDirFound) {
createdLogDir = createDirectory("/reports/OpenVAS")
} else {
}
dateDirFound = isDirectory("/reports/OpenVAS/" + runDate)
if(!dateDirFound) {
createdDateDir = createDirectory("/reports/OpenVAS/" + runDate)
} else {
}
saveToFile("/reports/OpenVAS/" + runDate + "/" + runDate + "-" + hostIP + "-OpenVASScan.pdf", reportData)
}
}
# If email is requested - zip, email, then delete zip file
{
if(email == "yes") {
filesZipped = zipFile("/reports/OpenVAS/" + runDate, "/reports/" + runDate + "-OpenVAS.zip")
mailSent = sendEmail(Global.smtpServer, "587", "STARTTLS", Global.smtpAccount,, Global.smtpSecuritySender, Global.smtpSecurityRecipient, "OpenVAS Reports - " + runDate, "Attached, please find a zip file of the OpenVAS reports from the " + runDate + " run.", "/reports/" + runDate + "-OpenVAS.zip")
} else {
}
fileDeleted = deleteFile("/reports/" + runDate + "-OpenVAS.zip")
}
# Close Remote OpenVAS CLI
close(openVASCli)


Comments