
It’s a new year and it’s time to figure out what purchases, projects, and services your organization will need in the near future. No doubt, your wish list will far exceed your budget.
To meet your security needs within a budget, make sure you are investing enough in IT security by shoring up your identity and access management (IAM) program. In order to truly enable your business, you must first embrace security, and that means putting IAM at the core of your security program.
IT Spending Priorities Past and Future
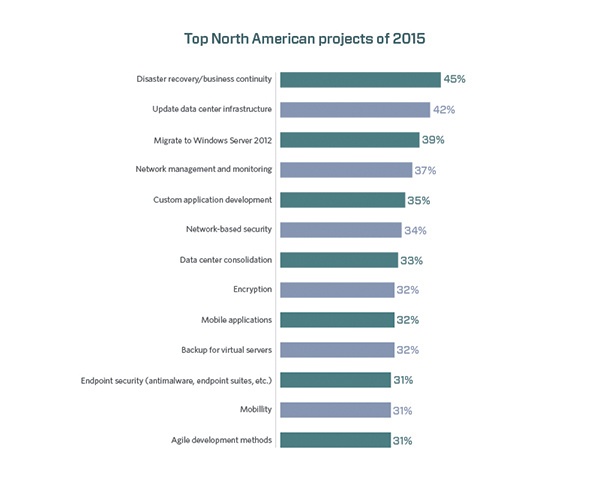
Before we look into our crystal ball, let’s take a look back over the years. As you can see in the bar graph from TechTarget’s annual survey, even as recently as 2015, IAM was not among the top IT priorities for North American companies. In addition, most security-related projects and investments were focused on protecting the perimeter.
However, many companies were planning projects that would fuel the need for better IAM in order to provide security in this evolving corporate environment. For instance, 30 percent of North American firms were planning to implement broad compliance initiatives in 2015. Additionally, 34% of organizations globally planned to implement mobility projects, such as BYOD initiatives.
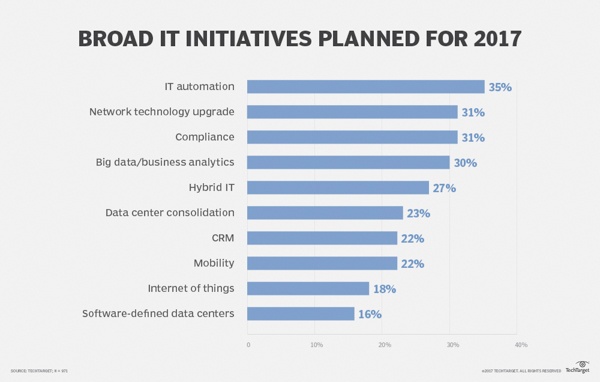
Fast forward to 2017 and we can see shift in priorities. Two security-related projects, IT automation and compliance, were in the top three IT initiatives planned for last year.
As the TechTarget annual IT priority survey illustrates, security has become a much more important concern for IT professionals in the last couple of years. Across all company size segments, security finished in the top three for how the IT respondents devoted their time, reflecting the perilous nature of global technology-driven commerce and the new corporate environment.
Where to Invest in 2018
So what should your IT spending priorities be for this year? Certainly, security needs to be at the top of your list. Here are the top security areas to invest in this year:
1) Cover Your Identity Security Basics
The 2017 Verizon Data Breach Investigations Report (DBIR) found that 88 percent of hacking-related breaches leveraged stolen and/or weak passwords.
We recommend taking some basic steps to ensure your doors and windows are locked. This includes using two- or multi-factor authentication, keeping software patched and up to date, encrypting sensitive data, securing privileged accounts, conducting ongoing organizational training, and having a plan of action for an attack and/or breach.
Implementing modern IAM tools helps minimize your attack surface and stop unauthorized access to critical systems. MFA, for example, can eliminate vulnerabilities from stolen and/or weak passwords across your critical networks, applications, and servers.
2) Eliminate Tedious Identity-Related Tasks with Automation
This is the year you should scrap scripts and manual processes for account requests and creation. Instead, automate these processes for improved efficiency and enhanced security.
While scripts are an easy short-term fix, they can create long-term headaches. For example, often one person is responsible for the scripting needs of an organization. If that person leaves or is unavailable, there may be no one else to manage the system or fix potential issues. Additionally, while that person may have a solid understanding of IT and scriptwriting, they are likely not an expert when it comes to the complexities of identity management and security best practices.
Now is the time to break out of the cycle of scripting, before it winds up endangering your entire organization.
Modern IAM software can help with automating repetitive tasks and save you time, money, and resources. The software automates account creation, password changes, and just-in-time user provisioning and deprovisioning.
The software allows you to reassign control of new account creation, role and group assignment, and access requests from the IT team to appropriate business managers. You can also set up self-service capabilities, so that users can perform common tasks, such as password resets, themselves. This will take the burden off of your IT department.
3) Get Serious About Governance
If you are not already prioritizing compliance, you had better start. The penalties for noncompliance have increased significantly. For example, violation of the security and privacy rules of the Health Insurance Portability and Accountability Act can result in fines in the hundreds of thousands if not millions of dollars.
The key to governance and compliance is to take a security-first mindset, rather than just checking a box, because the costs of a breach are much more than just fines.
According to the Ponemon Institute’s annual data breach cost study, the average cost of a data breach to a U.S. company in 2017 was a record high of $7.35 million, up 5 percent from the previous year.
You should consider continuous access certification. With thousands of entitlements and hundreds of systems, access certification audit campaigns can be complex, time-consuming, and prone to errors.
A modern IAM solution will offer both annual and continuous access certification campaigns to improve security by ensuring entitlements are always up-to-date, while reducing the cost, complexity, and workload associated with remaining compliance.
How Much to Invest
Now you know where to invest this year—but how much should you invest?
Gartner is forecasting that IT security spending will reach $96 billion in 2018, up 8 percent from 2017, driven by increasing security risks. Spending on IAM technology is expected to surge from $3.9 billion in 2016 to $4.7 billion in 2018.
According to a 2016 Forrester survey, this spending on IAM technology accounts for 9% of an enterprise firm’s overall IT security budget on average. 46% of those surveyed expected their IAM budget to grow by at least 5% over the course of the year.
From a numbers perspective, companies with fewer than 1,000 employees planned to spend $1.6 million on IAM technology; companies with between 1,000 and 9,999 employees budgeted $2.5 million for IAM; and companies with more than 10,000 employees earmarked $3.4 million, according to a Gartner survey of 298 companies in 2016. These numbers are in line with what we think you should be spending on IAM this year.
Looking ahead, Gartner expects more than 80 percent of organizations to use IAM software by 2019, up from 55 percent in 2017.
Back in 2015, IDC recommended that companies spend around 13.7 percent of their IT budgets on security technology, outside services, and staff, instead of the average of just under 10 percent.
With the current threat environment, we think that figure should be closer to 15-20 percent when taking into consideration the current cybersecurity risks that face both large and small organizations. Saving money today is not worth the price tag tomorrow.


Comments