 While best practice security policies and technology help to better secure an enterprise’s critical systems and data, the added disruption, inconvenience, and effort required by this stepped-up security often create real headaches and bad feelings toward the new policies and technologies.
While best practice security policies and technology help to better secure an enterprise’s critical systems and data, the added disruption, inconvenience, and effort required by this stepped-up security often create real headaches and bad feelings toward the new policies and technologies.
This is described as a “general hatred of security,” by Mike Pinch, the chief information security officer at University of Rochester Medical Center (URMC), in a presentation to the URMC Security Council.
A Real-World Example
Pinch developed a security hatred index based on feedback he received at URMC from his users—in this case, their provider population. The introduction of antivirus software prompted a slight increase in the index, use of encryption bumped it up, and a requirement for users to regularly change passwords pushed up the hatred index further.
But what really pushed up the index? The introduction of multi-factor authentication (MFA) without SSO doubled the hatred index from the level reached by frequent password changes. Basically, it was just another security step with no added benefit for the user population.
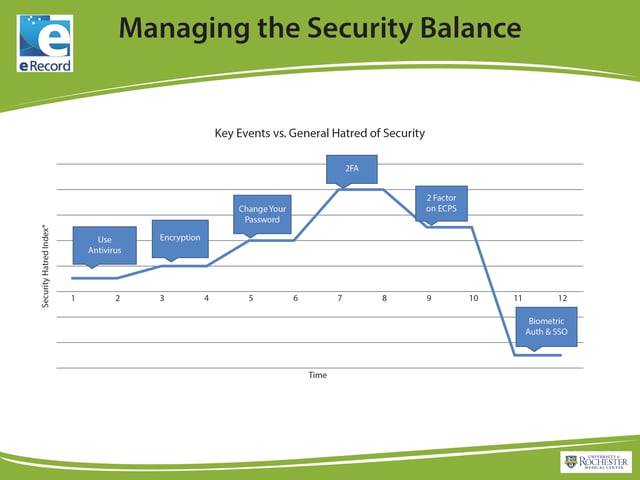
The reality is that security for the sake of security is rarely well-received. However, when URMC deployed technologies that also improved end-user experience, such as adding two-factor authentication to their Electronic Prescriptions for Controlled Substances (EPCS) system, the hatred index dropped because it reduced the amount of paperwork that was needed.
An even bigger decrease in the hatred index occurred when fingerprint biometrics and single sign-on (SSO) methods were implemented. These changes offered users the most benefit; streamlined authentication and a reduction in password fatigue saved users time and effort, while moving the security increases behind the scenes.
What to Avoid
Unfortunately, user hatred of best practices in security policies and technologies causes many companies to pull back from implementing MFA. A RAND study found a number of factors that can derail an MFA initiative:
- Implementation costs and friction: MFA is not free. In addition to system software costs, the per user cost for one time password tokens can run between $50 and $100. Managers may have heard that MFA can be easily evaded, or they view their current security practices as not needing repair.
- User resistance: Employees and other users may rebel against the restrictions, inconvenience, and difficulties associated with MFA compliance, raising the cost of implementation and the odds that it will be circumvented.
- Customer resistance: While employees might have to endure poorly designed MFA, frustrated customers will likely go somewhere else.
- Bad experience: A company may have already implemented MFA and gone through a bad experience with a previous vendor.
- Liability issues: Companies may believe that all they need is one-factor authentication to comply with legal requirements for due diligence, while implementing flawed MFA might open them up to legal liability.
The problem with any poorly implemented security measure is that users will find workarounds if they are frustrated, such as staying logged in, sending files to personal email accounts, writing down passwords, downloading data onto an external memory stick or drive, logging on to the network from an insecure Wi-Fi, and telling colleagues their passwords.
Users are not being malicious when they do these things; they are trying to get their jobs done with the least amount of hassle. But these shortcuts increase risk factors for their company.
Striking the Right Balance With Your Own MFA Initiatives
It is important to keep any security project from being too IT-centric; the user experience must be front and center. To drive adoption of your MFA initiatives, you need to sell users on the ways the project will improve end-user productivity and offer departmental benefits. Your users want to know how these new ways of authenticating will save them time and effort, even if they are being implemented to enhance security.
You also must give users technology that’s easy and flexible to use.
Adaptive authentication and flexible authentication policies provide this frictionless user experience. Adaptive authentication takes into account contextual factors and adapts the authentication process based on the risks involved. So, your users will only be asked for additional authentication when it is necessary for security purposes. And flexible authentication policies give users a choice in authentication methods, which meets the needs of your users, while still ensuring security.
Successful MFA implementation methods require smart policy, a good rollout, a comprehensive adoption strategy, and the right technologies. If you miss any of these methods, you will struggle to see the MFA adoption and return that you want. Instead, you will see resistance that only weakens security.
Modern identity management and MFA platforms provide choice and flexibility. The key is to strike the right balance between security and usability. This will lower the security hate factor among your employees and customers, while improving overall security for your organization.

Comments