In past posts, we’ve talked about how evolving business and threat landscapes have necessitated more robust, modern, and integrated Identity and Access Management (IAM) solutions. The reality for organizations today is that the weakest link in deterring security threats, such as system breaches and data theft, are employees themselves. Whether intentionally or unintentionally, employee data leaks are startlingly common and can have devastating effects on an organization.
Identity Automation Blog
Blog Categories
- Cybersecurity (134)
- Company News (101)
- K-12 Education (80)
- RapidIdentity (71)
- Multi-Factor Authentication (69)
- Higher Education (44)
- Identity Governance (43)
- Identity Lifecycle Management (32)
- Single Sign-On (32)
- Healthcare (29)
- Access Management (19)
- Government & Public Sector (5)
- Identity Automation Pathfinder (1)
5 IAM Metrics That Every Retail Organization Should Be Tracking
The easiest way to show success is through tangible measurement. When you roll out a new project or implement a new system, you can say that you think it’s working, but without evidence, you really can’t be sure. That is why metrics are so important to a business. Metrics enable an organization to know if productivity is up or if costs are down. They can also measure whether security has improved and identify opportunities to enhance processes. These reasons are precisely why it is so crucial to track identity and access management (IAM) metrics.
Zero-Day System Onboarding for Seasonal Workers
According to NRF, the retail industry annually hires between 700,000 and 750,000 seasonal workers for the holiday season. There is no reason to think that 2016 will be any different, with many retailers already ramping up their recruiting efforts for the November and December sales push.
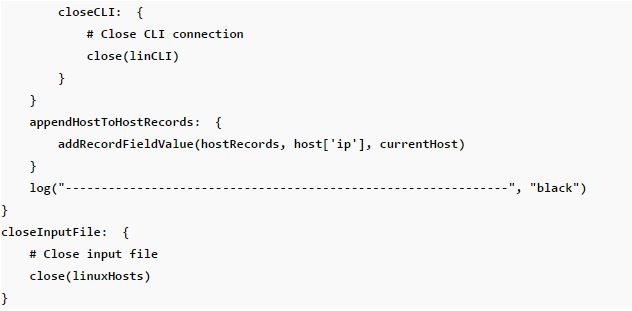
Managing Infrastructure with RapidIdentity Part 2: Managing Linux Hosts
Information technology teams tend to have a lot on their plate in terms of installing, maintaining, and protecting various systems throughout the enterprise. The larger the environment, the darker the cloud that tends to loom overhead when it comes to managing even trivial tasks, such as installing management agents or antivirus and keeping them up-to-date. Typically, this is due to the fact that there simply aren’t enough hands on the team, nor hours in the day, to touch dozens or hundreds of machines in disparate datacenters.
Making the Case to Your CIO to Upgrade Your IAM System, Part 3
Now that we’ve covered the business and technology trends and the evolving regulatory and budgetary challenges driving the need for a modern, robust IAM solution in the enterprise, it’s time to look at how they all fit together in an IAM upgrade pitch to your CIO.
Identity Automation Acquires 2FA, Inc. Adding Powerful Authentication Capabilities to our IAM Portfolio
I am excited to share our latest press release announcing that Identity Automation has acquired, 2FA, Inc., a cybersecurity company that specializes in multi-factor authentication and enterprise single sign-on (SSO).
Why Most Enterprise Password Management Policies Fail
From the massive Target data breach in 2013 to the Wendy's, UC Berkeley, IRS, and U.S. Department of Justice breaches of 2015 and 2016, today's enterprise exists in a security minefield in which a single misstep could lead to a massive breach and public blowout. As IT departments shutter and make sure to shore up their perimeter security, unfortunately, many overlook the fact that it was actually legitimate user credentials that were used in most 2016 data breaches, with some 63% being the result of weak, default, or stolen passwords, according to the new Verizon Data Breach Investigations Report (DBIR). These results drive home the point that passwords are the weakest link in the security chain and malicious intruders know it.
Expanding Our Footprint in Q2 with RapidIdentity as a Service
In Q2 2016, our new bookings of annual recurring revenue under contract increased 139 percent year-over-year. With the quarter behind us, I thought I’d share a few accomplishments from the past few months that have contributed to this exceptional growth.
Managing Infrastructure with RapidIdentity Part 1: The Basics
At Identity Automation, we focus on providing solutions to meet a wide variety of our customers’ needs. As our name implies, “Automation” is an important aspect of our belief that consistent, repeatable activities are key to any successful IT endeavor. Our RapidIdentity product set allows our customers to follow in that mindset and to build, test, and deploy highly tailored and effective management tools quickly, efficiently, and creatively. This all helps to minimize an organization’s staff efforts, while maximizing productivity.
How to Avoid a Zombie Account Apocalypse with IDM
They’re there, lurking, seemingly lifeless, clinging to the shadows. Even just one of them is dangerous, but when they amass in a horde, they can become an overwhelming throng of chaos, destroying everything their path.
Sounds like fiction, right? Well, unfortunately this type of zombie – zombie accounts – is all too real.
current_page_num+2: 32 -