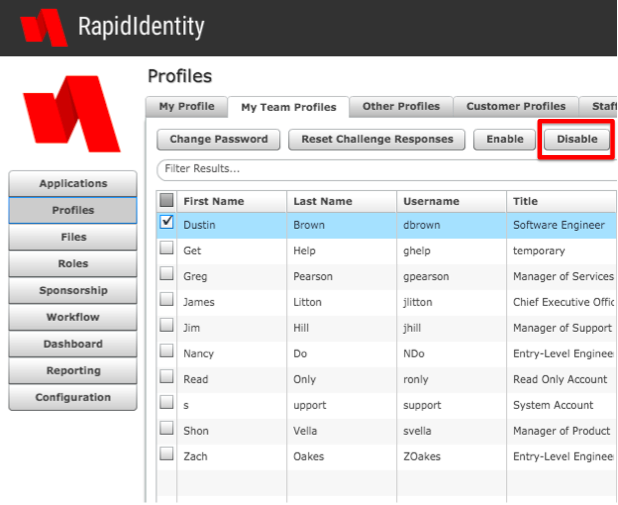
We’ve previously discussed the merits of automating the de-provisioning process. But even when automated, sometimes it can still take HR weeks to initiate the off-boarding process of a terminated employee due to alignment with their organizational payroll cycles. From a security perspective, allowing terminated employees to continue to access organization systems for weeks, days or even hours can present significant security risks.
Identity Automation Blog
Blog Categories
- Cybersecurity (134)
- Company News (101)
- K-12 Education (80)
- RapidIdentity (71)
- Multi-Factor Authentication (69)
- Higher Education (44)
- Identity Governance (43)
- Identity Lifecycle Management (32)
- Single Sign-On (32)
- Healthcare (29)
- Access Management (19)
- Government & Public Sector (5)
- Identity Automation Pathfinder (1)
Efficient De-Provisioning: Automation and Other Considerations
Organizations are typically very committed to removing an ex-employee from payroll systems when their employment has ended. No company wants to accidentally give money away to someone who no longer works there. Yet, we rarely see the same efficiency when it comes to de-provisioning that ex-employee from network systems, applications, and all other IT resources. Orphaned accounts can go unnoticed for weeks, months, and sometimes even years.
Identity Automation a Finalist for EdTech Digest 2016 Cool Tool Award for Security & Privacy Solution
We’re honored and happy to announce that RapidIdentity was selected as a finalist for the 2016 EdTech Digest Award in the Security and Privacy Solution category. The year just keeps getting better! In January our deployment with the North Carolina Department of Public Instruction (NCDPI) was recognized as a best deployment of the year.
James Litton Talks IAM on Texas Business Radio
Earlier this year, James Litton, our CEO, appeared on Texas Business Radio, the syndicated radio show that features leading businesses, people, and events from the Texas business world.
Three Tips for a More Secure 2FA Program
Last month I read an article reporting that researchers found two-factor authentication to be insecure and vulnerable to hacks. My initial reaction was skepticism, since it wasn’t recommending a more secure alternative like multi-factor authentication, but instead simply stating 2FA isn’t secure.
Contingent Workers Need Security Training Too
We’ve been talking a lot about the growing contingent workforce and what that means for management and IT when it comes to security and risk. Earlier this month, our CEO, James Litton, wrote a post about the need for basic security training at all levels of an organization. Today, I want to bring the two topics – contingent workers and security training – together.
Lincoln County Schools Secure Data, Boost Productivity with Identity Automation
How to Keep Employees from Sharing User IDs
If you’ve recently been employed in any kind of retail environment, you know that the use of passwords isn’t confined to white collar corporate desk jobs. Computer systems are used by all types of businesses and workers, which means passwords are a reality for all of us. Yet a unique aspect of the retail industry I’ve noticed is how prevalent it is for floor workers to share their user IDs or even have a shared login and password. Think about it. Have you ever seen a sticky note with some sort of “Password123” written on it in the corner of the point of sale (POS) register while you were checking out?
WEBINAR: A Trojan Horse of a Different Color: The Inherent Security Risk of Today’s Contingent Workforce
From seasonal employees to specialized contract workers, employment of contingent workers has dramatically increased in recent years. With 46% of businesses adding contingent workers in 2015, this workforce has proven to be resourceful, necessary, and here to stay. While there are clear benefits to this type of employment, there are also major security risks if the access of these employees is not properly managed.
Major Breaches in Healthcare and Government Highlight the Need for Increased Investment in Security Training
The breaches of Hollywood Presbyterian Medical Center and the United States Office of Personnel Management (OPM) have been hot topics in the last month. Hollywood Presbyterian because it’s so fresh in our minds and the OPM because of the fallout resulting from it, including House Oversight Committee hearings and the (forced) resignation of its CIO.
current_page_num+2: 36 -