In IT security, it’s often said that a company’s employees are its weakest link. As technology grows increasingly user-friendly, and the rules of digital “ownership” blur, rogue employees—those who don’t follow the standard IT security rules for one reason or another—are emerging as a significant threat to corporate security.
At your organization, IT assets are likely well-protected by firewalls, network segmentation, and data security software, including email security, antivirus, antimalware, and data loss prevention (DLP) solutions. But what would happen if employees were intentionally sending valuable data off-site? What impact would this type of rogue behavior have on overall IT security?
The Threat
These days, there’s no question that you should be concerned about rogue employees. They pose a real threat to your organization.
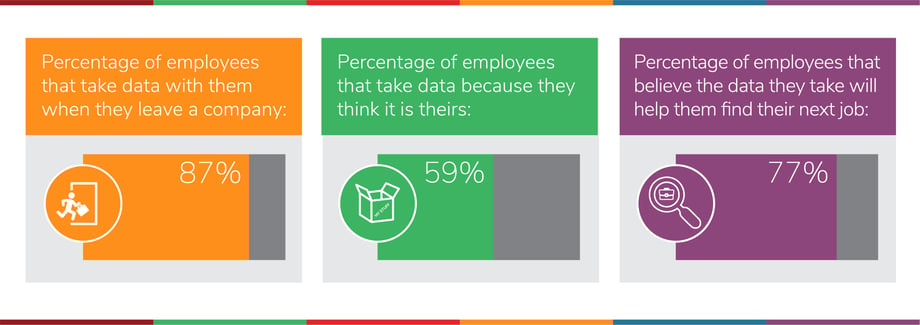
Consider a recent survey that found an astonishing 87 percent of employees admit to taking data they created with them when they leave a company. The data ranges anywhere from Microsoft Office documents to financial information, legal documents, and multimedia. Most often, employees email data to themselves, use a secure file transfer or FTP, or even take photos of documents using a smartphone.
A salesperson may take his contact list to use at his next job, or a marketer may collect projects in process to add to her portfolio. A recent case in the U.K. provides a real-life example: Before leaving her job to join a competitor, an employee forwarded the details of 100 clients and potential clients to her personal email, so she could leverage them in her new position.
Why do employees behave this way? In most cases, they are stealing information intentionally, either because they feel entitled to it or believe taking it is permissible. Fifty-nine percent of survey respondents said they take data because they feel that it is theirs. Seventy-seven percent admitted that they thought the information would help them find or get ahead in their next job.
As we discuss in our e-book “The 3 Types of Rogue Employees—and How to Stop Them,” other rogue employees are simply being careless with information, and a few are bent on intentionally harming the company. Many feel less loyalty to a company that they are leaving; others are flat-out bitter.
Security Concerns
The actions of just a few rogue employees could put your organization in serious jeopardy. In fact, a report by the International Business Times found that 37 percent of IT professionals said rogue employees are the biggest threat to information security—higher than external threats such as cyberattacks and BYOD.
In our digital age, every company needs to protect its assets, especially as data breaches and hacking attempts grow increasingly frequent and sophisticated. With untold amounts of data streaming out your doors, intellectual property, customer data, and other important information could be out in the open, having circumvented all typical security measures.
This exposes you to potential data breaches, ransomware attacks, sabotage, and more. In industries, such as healthcare and banking, where data privacy is an absolute must, you may fall out of compliance. And, the potential impact of these risks is far-reaching: lost revenue, tarnished reputation, regulatory fines, and ruined careers.
What to Do about It
While it may be impossible to prevent every incident of employee data theft, you can significantly reduce your company’s vulnerability to it. A well-defined policy, combined with identity and access management (IAM), can help to cut down on data leaks from apathetic or entitled employees, while also combating the malicious ones.
Modern IAM solutions are vital for protecting a company against rogue employees. Handling identity access on an as-needed basis leaves too many gaps—and that’s how employees are able to steal important data.
A comprehensive IAM program includes key capabilities that provide full lifecycle management of all users, which improves data security company-wide:
- Automated deprovisioning: When worker, full-time, part-time or even on contract leave an organization, their access to all systems, resources, and assets is automatically removed. This is particularly important for companies that use cloud-based systems and applications.
- Automated role- and attribute-based entitlements: Often a user will be granted access to additional networks or systems for a certain job role or project. Without a full IAM program, that entitlement may be in place for as long as a user stays with the company. But modern IAM automates the addition and removal of entitlements based on roles and attributes. So, if an employee’s role shifts, his or her entitlements are automatically updated, closing gaps that otherwise encourage data theft.
- Delegated administration: Modern IAM solutions delegate the administration of key systems, empowering managers or system owners to grant or revoke access. This eases the burden on IT, putting the power into the hands of the most appropriate people to monitor and manage access to sensitive data.
- Audit trail: Tracking who accesses what, where, and when provides important evidence in the event that data is stolen. This capability can also be used proactively; for example, if your organization is anticipating layoffs and you want to keep a close eye on specific systems.
Together, these capabilities significantly increase protection of systems, applications, and data. An effective IAM program discourages employees from stealing information—regardless of their motivation.
Learn More
Wondering what rogue employees may work at your company? Learn how to spot the different types of rogue employees—and how to safeguard against them—in the e-book “The 3 Types of Rogue Employees—and How to Stop Them.”


Comments