Phish Wire - January 19, 2026

Between January 01, 2026 and January 16, 2026, analysts identified a concerning surge in sophisticated multi-stage credential harvesting campaigns targeting high-profile brands including Microsoft, American Express, Amazon, Adobe, and Netflix, with attackers demonstrating increasingly advanced evasion techniques and infrastructure abuse. The most notable trend observed was the widespread adoption of multi-stage authentication bypass tactics, where threat actors first capture primary credentials through realistic brand impersonation, then immediately collect OTP/2FA tokens via secondary forms posting to endpoints like "process.php," effectively defeating modern multi-factor authentication protections across targeted organizations.
Sophisticated techniques included extensive JavaScript obfuscation with base64-encoded payloads, Unicode character substitution for text-based detection evasion, anti-analysis measures such as developer tools blocking and debugger detection, and the abuse of legitimate cloud services including Cloudflare Workers and Backblaze B2 for hosting malicious content. Infrastructure analysis revealed a shift toward compromised legitimate domains and professional development frameworks utilizing Bootstrap, jQuery, and responsive design elements that create pixel-perfect brand replicas, while several campaigns employed proxy-based man-in-the-middle architectures enabling real-time session hijacking beyond simple credential theft. The emergence of comprehensive phishing kits capable of impersonating multiple email providers (Outlook, Office365, Gmail, Yahoo, AOL) within single campaigns, combined with personalized victim targeting and realistic error simulation to encourage multiple credential attempts, represents a significant escalation in threat sophistication that poses elevated risk to organizations relying on traditional email security and user awareness controls.
Domains Reviewed
- www[.]ameuricanrpures[.]com/k7mzm42y3mpnvp35zy/dhec3t7xx22s/gmj9smnqqb7o... (2 variants)
- prime[.]support[.]id[.]20-244-4-78[.]cpanel[.]site/desktop/ap/signin?ref...
- owolambowhite[.]com/8GPKGDBblHWFx6w476nwsJjHb5sN2X4naOBJuOcYr9kVdkI3reEj...
- theme[.]thaililo[.]net[.]im/5fdmex5wmn?c03d26ef7fc2925c-c60f9a8171b8ce46...
- welcbustinvita[.]es/part_ksq/AcrobatN/
- f005[.]backblazeb2[.]com/file/seeeedeeded/onedr-updated[.]html
- biizzlive[.]it[.]com/come/s/Biz/
- mochiss[.]xyz/fr-en/login?serverState=%7B%22realm%22%3A%22growth%22%2C%2...
- www[.]competenle[.]de/piza/invitation/
- 4rh8jzfe[.]amdaretta-utko2[.]workers[.]dev/?alexis[.]logan@fleming[.]kys...
- files[.]jandhan[.]cfd/new/password[.]php
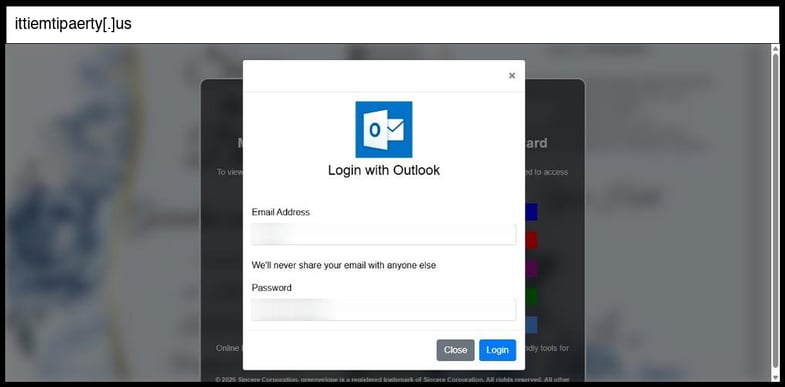
- ittiemtipaerty[.]us/topenjoy/ondeck/
- www[.]ameuricanepruexs[.]com/3zm7kk1o2y2v7yd_/j95sjx71h5hz3e04vv/kjmbl-r...
On January 15, 2026, an employee at a Illinois organization clicked the below phishing page.
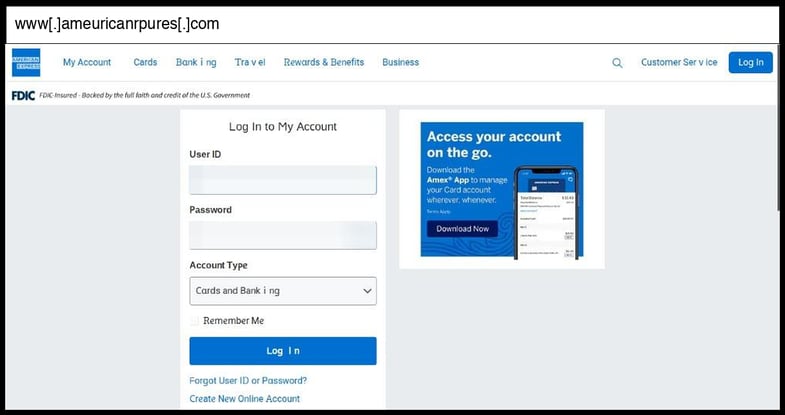
This phishing page uses a basic HTML form that likely submits credentials via standard POST method to capture American Express login details, though the actual submission endpoint is not visible in the provided HTML code. The most significant TTPs observed include sophisticated visual mimicry using corrupted Unicode characters in the title and navigation text (e.g., "áªoÉ¡ Ðᥠto Ðy áªÑÑouá¥t" instead of "Log In to My Account") to evade text-based detection systems, comprehensive CSS styling that closely replicates American Express's legitimate login interface including proper color schemes (#006fcf blue) and responsive design, and social engineering through familiar login form elements with account type dropdown options and "Remember Me" functionality.
The page appears to be a static HTML/CSS implementation hosted on a suspicious domain (ameuricanrpures.com - a typosquatting variant of American Express) with a complex obfuscated URL path, representing a moderate sophistication level due to the Unicode evasion technique and professional visual design, though it lacks advanced JavaScript-based credential exfiltration or real-time validation features.
Additional similar attacks were clicked:
- www[.]ameuricanrpures[.]com/ffwdfgv1oer7n4c/c7ct6_8p2jk706isi9/htoa2w7-_jk-/hpt5birg057o5t8kxb/4b6cc414452f661289d4909cbc53658e55ef506eaa573...
On January 14, 2026, an employee at a Utah organization clicked the below phishing page.
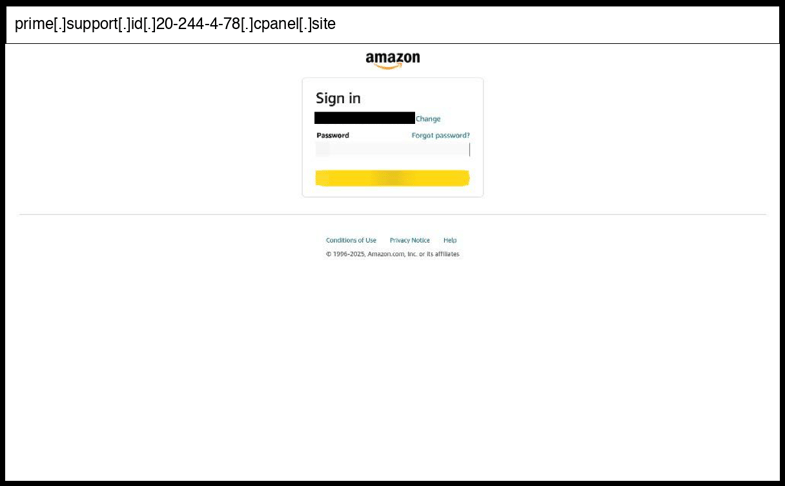
This is a basic credential harvesting phishing page that uses a standard HTML form (id="signIn") that POSTs credentials to the same malicious URL path ("/desktop/ap/signin") when submitted. The page employs sophisticated visual mimicry of Amazon's sign-in interface using embedded base64-encoded Amazon logos and CSS styling that closely replicates the legitimate Amazon login experience, including proper form validation messaging and UI elements.
The infrastructure appears to be hosted on a compromised or maliciously registered domain (20-244-4-78.cpanel.site) that mimics hosting service naming conventions, and the URL contains a suspicious long reference parameter that may be used for tracking victims or campaign identification. The sophistication level is moderate due to the high-quality visual reproduction of Amazon's interface and the professional CSS implementation, though it relies on basic form submission rather than advanced JavaScript exfiltration techniques. The page lacks obvious evasion techniques like geofencing or anti-analysis measures, making it a straightforward but well-crafted credential harvesting operation.
On January 14, 2026, an employee at a Nevada organization clicked the below phishing page.
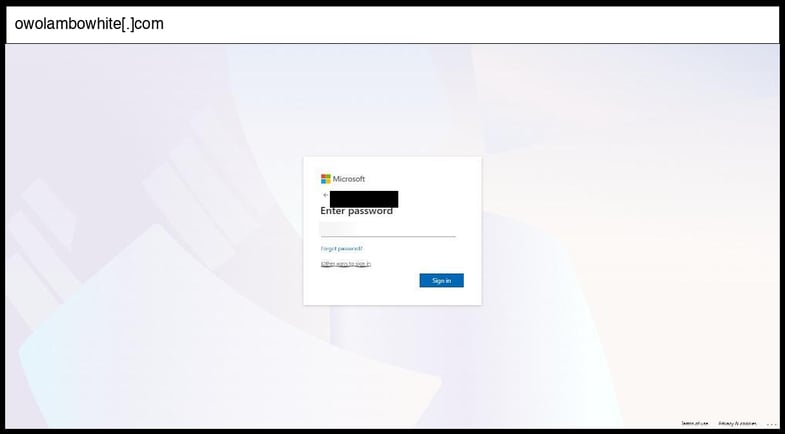
This is a sophisticated multi-stage Microsoft phishing page that captures credentials through JavaScript form handlers that appear to exfiltrate data via fetch/XHR requests to external endpoints, with the primary capture mechanism being JavaScript-based rather than traditional form POST submission. The page implements several advanced evasion techniques including extensive code obfuscation with base64-encoded configuration strings (var_options_242, var_params_248), randomized CSS class names and element IDs to evade detection signatures, anti-bot honeypot fields with the "a_item_884" class, and user selection restrictions with right-click/text selection disabled.
The infrastructure leverages multiple external JavaScript dependencies including jQuery and resources from cdn.statically.io, with Cloudflare CDN services for performance and additional obfuscation, while the complex multi-section flow mimics authentic Microsoft login flows including MFA/2FA collection through authenticator apps and SMS codes. This represents an advanced sophistication level due to its comprehensive anti-analysis measures, realistic Microsoft UI replication with proper branding and loading animations, and sophisticated JavaScript architecture designed to capture not just usernames/passwords but also multi-factor authentication tokens across multiple verification methods.
On January 13, 2026, an employee at a Kentucky organization clicked the below phishing page.
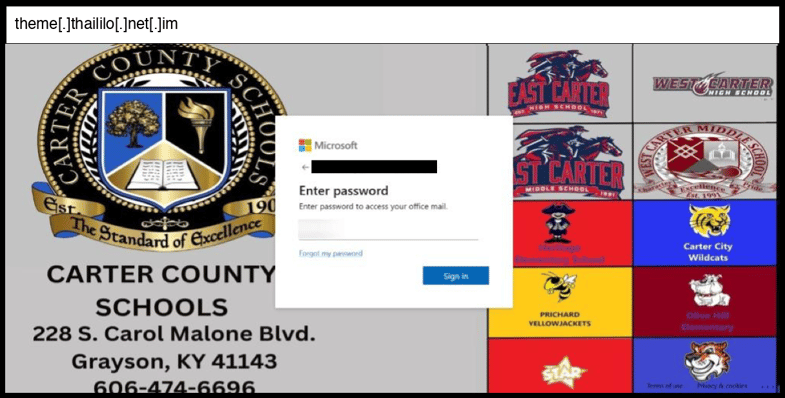
This phishing page uses JavaScript-based credential exfiltration through an obfuscated script that contains a large base64-encoded payload in the variable "ag", which is likely decoded and executed to capture credentials without traditional form submission. The page implements several evasion techniques including a copy event handler that prevents users from copying content (replacing clipboard data with just "c"), hidden content with misleading loading messages, and appears to impersonate Microsoft authentication services based on the background image URL from "aadcdn.msauthimages.net".
The infrastructure shows signs of compromise or malicious hosting on the "thaililo.net.im" domain, and the sophistication level is moderate given the heavy obfuscation of the main payload, though the actual credential capture mechanism would require decoding the base64 string to fully analyze. The presence of fake GoGuardian security scripts and the Microsoft branding suggests this targets corporate or educational environments where users might expect to see both authentication flows.
On January 12, 2026, an employee at a Kentucky organization clicked the below phishing page.
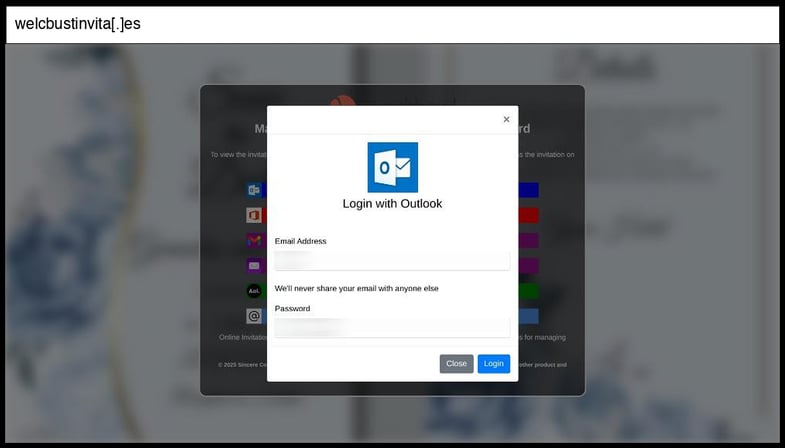
This phishing page uses multi-stage credential harvesting by initially capturing credentials via AJAX POST to "processmail.php" and subsequently collecting OTP tokens through "process.php", implementing a sophisticated two-factor authentication bypass technique. The site employs several social engineering tactics including fake Adobe branding, urgency messaging about viewing invitations, and a realistic multi-provider email login interface (Outlook, Office365, Gmail, Yahoo, AOL) with dynamic modal popups that adapt based on the selected provider.
The infrastructure shows signs of a compromised legitimate domain (welcbustinvita.es) with professional implementation including Bootstrap framework, Font Awesome icons, Cloudflare protection, and polished UI elements that mimic legitimate services. The sophistication level is moderate-to-advanced due to the multi-stage collection process, real-time form validation with error handling ("Incorrect Password" feedback), OTP collection with countdown timers, and the seamless integration of credential capture followed by MFA token harvesting - a technique commonly used to bypass modern authentication protections.
On January 12, 2026, an employee at a Kentucky organization clicked the below phishing page.
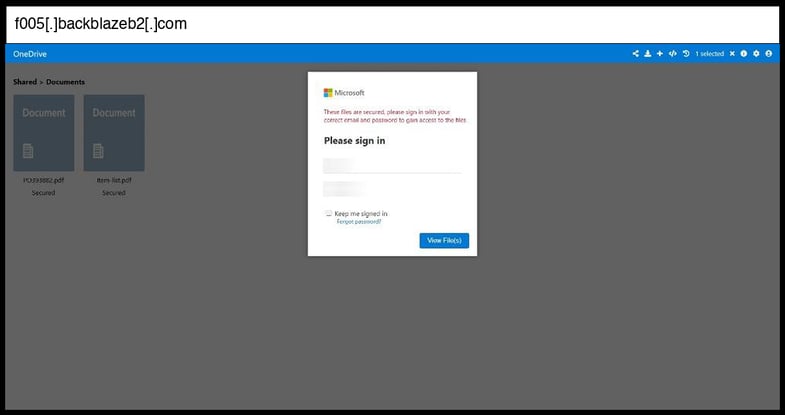
This phishing page uses a standard HTML form submission method to capture credentials, with the form configured to POST data to an endpoint (though the specific action URL is not visible in the provided HTML snippet). The page employs sophisticated visual mimicry of Microsoft OneDrive's interface, including authentic Microsoft branding, color schemes (#0078d4 Microsoft blue), and Segoe UI fonts to create a convincing replica.
Notable evasion techniques include CSS-based content overlay manipulation with z-index layering to obscure background elements and create a modal-like login experience, plus extensive CSS variable definitions that suggest this may be part of a larger phishing kit designed to impersonate multiple services beyond just OneDrive. The page is hosted on Backblaze B2 cloud storage (f005.backblazeb2.com), representing abuse of a legitimate cloud service provider, and includes responsive design elements and error message handling that indicate moderate sophistication in its construction. The presence of extensive theme-based CSS variables (th-wq, th-rw, th-eq, etc.) suggests this is likely a component of a multi-brand phishing framework capable of impersonating various services depending on configuration.
On January 09, 2026, an employee at a Kentucky organization clicked the below phishing page.
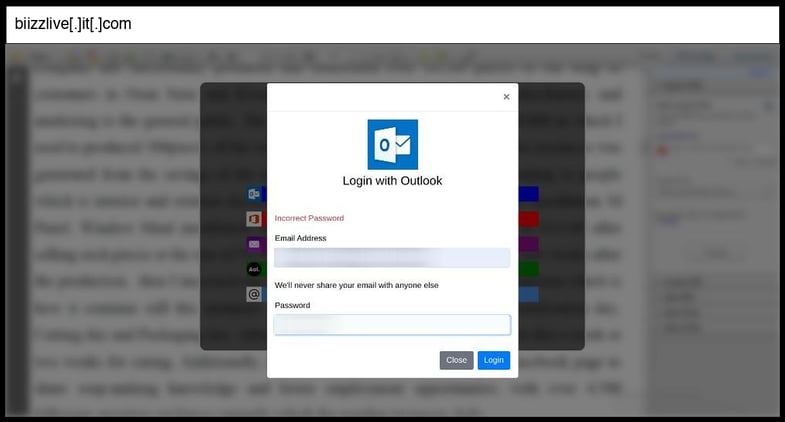
This phishing page captures credentials through a standard HTML form POST to "processmail.php" for email/password collection followed by a secondary form POST to "process.php" for OTP capture, implementing a sophisticated multi-stage credential harvesting operation that mimics Adobe Document Cloud and collects both primary credentials and two-factor authentication codes. The page employs advanced social engineering through brand impersonation of Adobe with authentic-looking logos and document access pretext, presents multiple email provider options (Outlook, Office365, Yahoo, AOL) with corresponding branding to increase victim trust, and uses jQuery AJAX submissions with fake "Incorrect Password" error simulation to convince victims to re-enter credentials if the first attempt appears to fail.
The infrastructure shows professional development with extensive CSS styling, responsive design, modal-based UI interactions, and integration with CloudFlare services, while the multi-stage approach specifically targets modern MFA-protected accounts by capturing both passwords and OTP tokens, representing a moderately sophisticated operation that goes beyond basic credential phishing to defeat two-factor authentication.
On January 09, 2026, an employee at a Florida organization clicked the below phishing page.
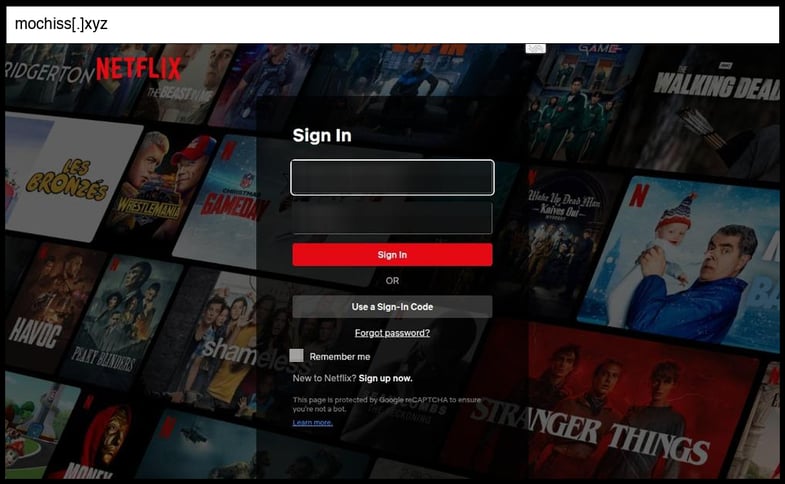
This phishing page uses a combination of form-based credential capture (likely POST submission) targeting Netflix authentication, while being delivered through a sophisticated proxy service hosted on mochiss.xyz that appears to be a malicious web proxy (similar to CroxyProxy) designed to intercept and relay traffic. The page implements several notable TTPs including complete Netflix UI replication with legitimate assets fetched from netflix.com domains, extensive JavaScript obfuscation and proxy functionality that creates a man-in-the-middle scenario, and integration with multiple advertising networks and tracking systems (deducecore.com, p23hxejm1.com, cobaltsanctionyodel.com) suggesting monetization through malvertising.
The sophistication level is moderate-to-advanced due to the proxy-based infrastructure that allows real-time session hijacking, the use of legitimate Netflix assets to create pixel-perfect impersonation, and the complex JavaScript framework that handles traffic routing and credential interception rather than simple form submission. Most concerning is the proxy service's ability to maintain persistent sessions and potentially intercept all user interactions with the legitimate Netflix site after credential theft.
On January 09, 2026, an employee at a Minnesota organization clicked the below phishing page.
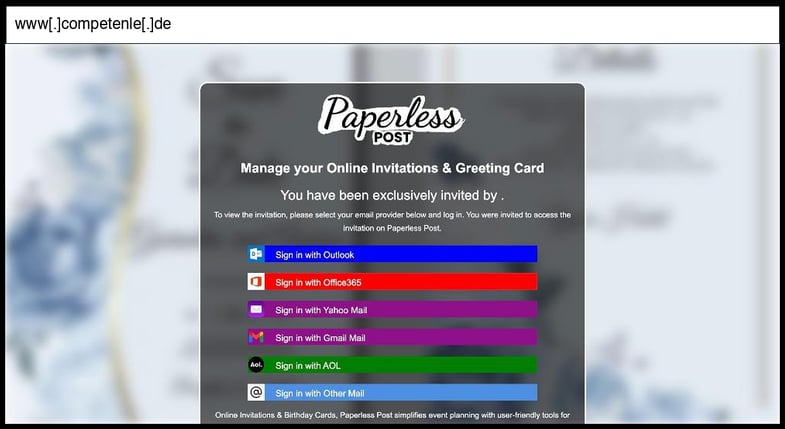
This phishing page uses a multi-stage credential collection approach that first captures email and password credentials via AJAX POST to "processmail.php", followed by a second stage that collects OTP/2FA codes via POST to "process.php". The page impersonates Paperless Post invitation service with sophisticated social engineering including personalized inviter names extracted from URL parameters, animated typing effects, and multiple email provider options (Outlook, Office365, Yahoo, Gmail, AOL) to increase victim trust.
The site is hosted on a suspicious German domain (competenle.de) that appears to be either compromised or specifically registered for this campaign, with one Gmail option redirecting to a separate subdirectory suggesting additional infrastructure. The sophistication is moderate, featuring deliberate "incorrect password" error simulation to encourage multiple credential attempts, OTP collection with countdown timers, and professional UI design with Bootstrap framework, though it lacks advanced evasion techniques or real-time validation against legitimate services.
On January 08, 2026, an employee at a Kentucky organization clicked the below phishing page.
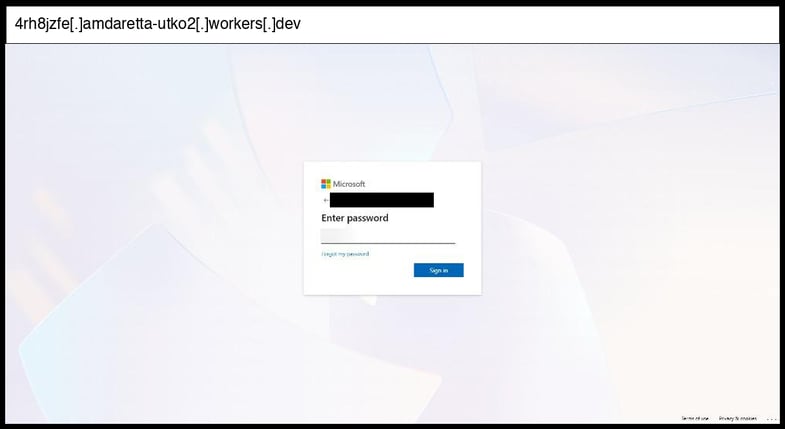
This phishing page employs a multi-stage credential collection process that captures Microsoft login credentials through form submissions to an unknown backend endpoint, with the collected data likely exfiltrated via JavaScript fetch() or XMLHttpRequest calls to the attacker's server. The kit demonstrates moderate sophistication through several anti-analysis techniques including developer tools detection (blocks F12, Ctrl+U, Ctrl+Shift+I), debugger evasion using performance timing checks that redirect to Zalando if debugging is detected, and clipboard manipulation that overwrites copied content with a random string "haNzvsuUdE".
The page is hosted on Cloudflare Workers (workers.dev domain) and meticulously impersonates Microsoft's Azure AD login interface with authentic-looking CSS, logos, and multi-step authentication flow including username collection, password entry, and various error states like "More information required" and "You cannot access this right now". The kit includes sophisticated visual elements like loading animations, proper Microsoft branding, and realistic error messages, while the URL structure suggests it's targeting a specific victim from Fleming County Schools in Kentucky, indicating this is likely a spear-phishing campaign rather than broad-spectrum credential harvesting.
On January 08, 2026, an employee at a Kentucky organization clicked the below phishing page.
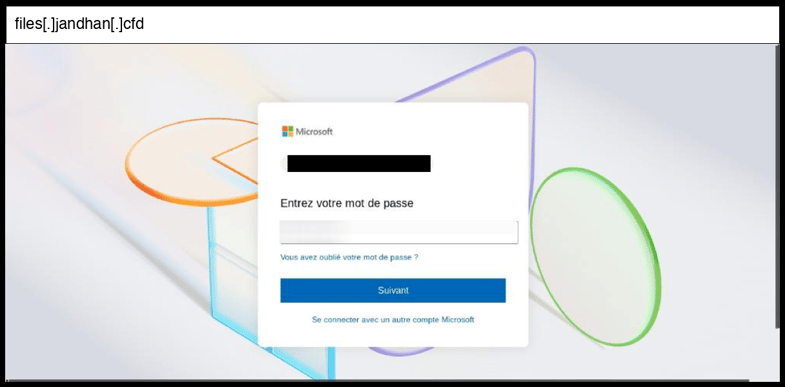
This phishing page employs a standard HTML form POST method for credential capture, submitting the harvested password along with a hidden email field to the same URL (password.php) when the victim clicks "Suivant". The page demonstrates sophisticated brand impersonation of Microsoft's login interface with authentic-looking styling using Segoe UI font, proper color schemes (#0067b8), and responsive design elements, while displaying the victim's actual email address to increase credibility through personalization.
The infrastructure utilizes the suspicious domain "jandhan.cfd" which appears to be a disposable hosting service, and includes Cloudflare's beacon tracking script suggesting the attackers are monitoring visitor analytics. The sophistication level is moderate, featuring well-crafted visual mimicry and personalization tactics, though it relies on basic form-based credential harvesting rather than advanced techniques like real-time validation or AiTM proxying.
On January 06, 2026, an employee at a Colorado organization clicked the below phishing page.
This phishing page uses a multi-stage credential capture method that initially submits credentials via AJAX POST to "processmail.php" and subsequently collects OTP codes through a second form posting to "process.php". The attack employs several sophisticated social engineering tactics including brand impersonation of Adobe and Greenvelope with legitimate-looking logos, a multi-stage authentication flow that first shows "Incorrect Password" on the first attempt to appear legitimate, and a convincing OTP collection phase with a countdown timer and loading animations to simulate real 2FA processes.
The page targets multiple email providers (Outlook, Office365, Yahoo, AOL) with provider-specific branding and implements a realistic user experience flow including modal dialogs, Bootstrap styling, and AJAX-based form submissions that prevent page redirects. While the basic infrastructure appears standard with PHP backend processing, the sophistication lies in the multi-stage psychological manipulation, realistic timing delays, and the seamless integration of credential harvesting with OTP collection to bypass modern 2FA protections.
On January 05, 2026, an employee at a Illinois organization clicked the below phishing page.
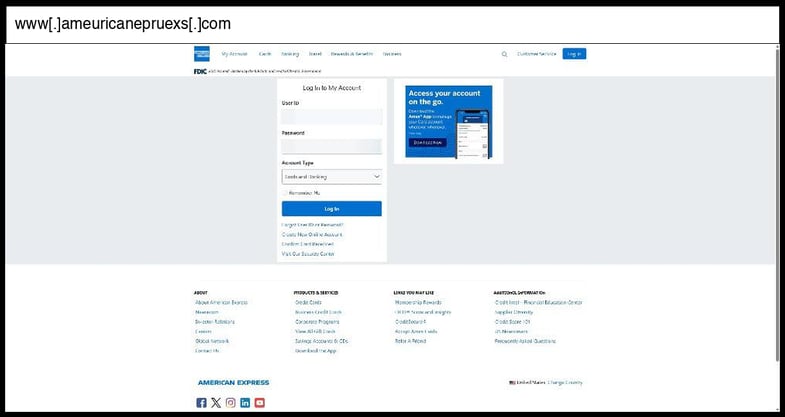
This phishing page uses a basic HTML form submission method for credential capture, with the form fields collecting username, password, and account type but no visible form action endpoint in the provided HTML snippet, suggesting the actual submission mechanism may be handled by the referenced JavaScript file (/static/js/main.89b592eb.js). The site employs moderate social engineering tactics including American Express brand impersonation with authentic-looking logos and styling, Unicode character substitution in text elements (e.g., "áªoÉ¡ Îá¥" instead of "Log In") likely for evasion purposes, and a sophisticated loading overlay system with professional styling to create legitimacy.
The infrastructure appears to use a typosquatted domain ("ameuricanepruexs.com") and includes comprehensive responsive design elements, favicon implementations, and a complex CSS framework that demonstrates above-basic development effort. The page includes a custom message overlay system and loading animations that suggest potential multi-stage interaction, though the actual credential exfiltration mechanism would require analysis of the JavaScript file to determine if it uses fetch(), XMLHttpRequest, or traditional form POST methods.
Recommendations
- Implement URL filtering to detect and block newly registered domains and typosquatted domains that mimic legitimate financial and technology services, focusing on domains registered within the last 30-90 days.
- Deploy email security controls to flag messages containing links to cloud storage services (Backblaze, Workers.dev) and proxy services when sent from external sources, requiring additional verification before user access.
- Configure web security gateways to detect and block pages using Unicode obfuscation techniques and anti-analysis measures such as developer tools blocking, clipboard manipulation, and debugger evasion scripts.
- Implement user awareness training specifically focused on recognizing multi-stage authentication phishing that collects both passwords and MFA codes, emphasizing that legitimate services never request OTP codes via email links.
- Enable conditional access policies that restrict authentication attempts from suspicious geolocations and require additional verification for logins preceded by email link clicks within a defined time window.
- Deploy network monitoring to detect and alert on POST requests to suspicious PHP endpoints (processmail.php, process.php) and AJAX calls to newly registered domains from corporate devices.
- Configure browser security policies to restrict JavaScript execution from untrusted domains and implement Content Security Policy (CSP) headers to prevent credential forms from submitting to external domains.




