At a certain point in your ongoing push to modernize security at your organization comes the moment of truth: time to present your initiatives, and your results, to your board of directors (BOD). In the past, you may have gotten by with little more than a cursory explanation, touching on little more than compliance issues, but in 2017, cybersecurity no longer flies under the BOD’s radar.
Identity Automation Blog
Recent Posts by Kathleen Garska
How CEOs Can Drive Adoption of Identity and Access Management and Other Cybersecurity Programs
By this point in our series on security and the CEO, it should be clear that security isn’t just a technological issue. It’s a cultural one, and you must improve your organization’s security culture, as well as its security processes and technologies. To accelerate your digital transformation, security must become part of your company’s very DNA. That’s where the CEO comes into play.
How RapidIdentity Protects Student Data & the EFF’s “Spying on Students” Report
Within every market—whether it be government, business, healthcare or education—it’s crucial that identity and access management (IAM) solutions are designed and implemented with close adherence to the latest government, regulatory, and best practice security frameworks and laws, in order to help organizations meet their compliance goals and to ensure the integrity and security of their user data.
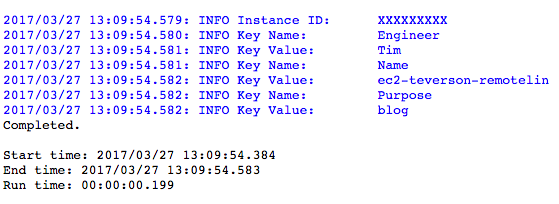
Starting, Stopping and Managing AWS Instances: Managing Infrastructure with RapidIdentity, Part VI
As more and more organizations realize the benefits of “cloud computing," the demand to host applications and services in the cloud continues to rise. Identity Automation and many of our customers have moved significant workloads into Amazon Web Services (AWS) or other cloud-hosted environments, and as a result, the need to automate and manage tasks in these environments has become more commonplace.
Amazon has provided management API’s to accommodate these needs and RapidIdentity allows customers to use them, in order to provide the same automation and “ease of use” in managing their cloud resources that they have come to rely upon for their day-to-day, on-premise IT processes.
Your Action Plan for Addressing Ransomware
In 2017, ransomware, the use of weaponized encryption to block access to a computer system or service until a ransom is paid, is all the rage among hackers. In fact, ransomware is now one of the top three most common malware threats.
The situation is dire, with hackers requesting ransoms of up to $73,000 per attack. Ransomware payments totaled more than $1 billion in 2016, a massive jump from the mere $34 million paid in 2015.
Ensuring Your Information Security Program Addresses Your Shadow IT Problem
A specter is haunting your business—the specter of shadow IT. It’s circumventing your security policies, compromising your data sovereignty, and costing you money. It lurks on your networks, on your employees’ computers and devices, on your servers, and in the cloud. Ever-present and always out of sight…or, at least, that’s how it sounds.
Executive Action Plan: 7 Steps to an Information Security Program
At this stage in your efforts toward modernizing your company’s information security program, it’s time to move beyond education and dialogue into more concrete action. By following these seven steps, you can pave the way toward a more secure future for your organization.
Ransomware: A Top Security Threat for Higher Education
2016 was the year of the hacker. From Russian hackers targeting US elections to the jaw-dropping compromise of more than 1 million Yahoo! user accounts and the DDoS attack that "broke the Internet," it seems like hacks and data breaches were in the news every day. Russian hackers aside, ransomware was the cybersecurity topic that captured the year’s headlines.
Identity and Access Management Terms Your C-Suite Needs to Know
Now that your C-suite understands your company’s information security program, it’s time to move further into the educational phase.
As you evaluate and prioritize the risks your organization faces, identity and access management (IAM) should become a clearer and clearer priority. To help you educate your CEO on the need for increased investment in modern IAM solutions, here is some key IAM terminology that you can use as you work to transition your company to a more modern strategy.
How Modern IAM Solutions Simplify Preferred-Name Changes
College and university IT teams are struggling with technical limitations that make it difficult to comply with evolving preferred-name policies—at least in a timely or automated manner—across a more complex digital environment. While it may seem like a student name change is a relatively easy task for an IT department, at the most recent EDUCAUSE annual conference, multiple schools expressed questions, concerns, and challenges regarding their ability to deal with preferred name changes in directory systems and downstream applications.
current_page_num+2: 12 -