
It’s no secret there are high expectations surrounding the healthcare industry, especially today with the state of emergency and fear bound to the COVID-19 Pandemic. Healthcare organizations must take even higher measures to protect patient and staff safety, deliver a high quality of care in an efficient manner, and keep patient records and information secure with adherence to compliance requirements.
As if that’s not enough, the healthcare industry also has a target on its back for cybersecurity threats— from social engineering attacks and phishing to ransomware and hackers. Cybercriminals are highly motivated to execute these attacks to gain access to employee and patient data because personal healthcare information (PHI) is worth significantly more than other types of information on the dark web, including credit card information.
By using compromised credentials, someone foreign to the organization can present themselves as a regular user with approved access to systems and applications. Therefore, when it comes to controlling access to applications, systems, and resources, identities must be at the center of healthcare’s security strategy.
So, how can healthcare balance robust identity-driven security, while also enhancing clinicians’ ability to readily access systems and applications for patient information?
The answer: Identity and Access Management (IAM). IAM is a set of tools, processes, and policies to ensure the right people have the right access to the right resources for the right amount of time to do their job.
In this blog, we’ll address the reality of IAM and where the main IAM tenets fall on the scale of enabling usability versus security. Let’s jump right in!
Redefining Identity Management
In many healthcare organizations, the perception of IAM is that it addresses account provisioning, which is just one capability of Identity Lifecycle Management (ILM). Others believe the general focus of IAM is authentication, federation, Single Sign-On (SSO), or password management.
While those areas are all important, in reality there are many, different facets of IAM and the capabilities are extensive in any organization.
At Identity Automation, we’ve identified the top three reasons why organizations typically focus on IAM:
- To improve security posture, which is a crucial element of the cybersecurity initiative in many organizations.
- To improve operational efficiency, a key area for healthcare, especially when streamlining clinical workflows to treat patients in a timely manner. Clinicians must keep patients safe and offer the best information, while providing their patients a great experience, so operational efficiency is key throughout that process.
- To improve the user experience for employees, or the people who are actually accessing your systems and applications on a daily basis. It’s important to provide your users with a simplified overall user experience because nothing frustrates people more than having to figure out where they need to go to login for each system and then to remember each password on top of that.
IAM Balance: Security vs. Business Enablement
In terms of the use of resources and applications, healthcare security typically comes with a usability sacrifice, which is certainly a challenge IT leaders face. We’re required to meet compliance and reduce risk, so we have to enforce security. However, we cannot let security affect patient care by hindering providers and clinicians from completing patient visits in an efficient manner, because that’s the top priority at the end of the day.
So, how do we reduce the risk through security without sacrificing usability, especially in regards to clinicians?
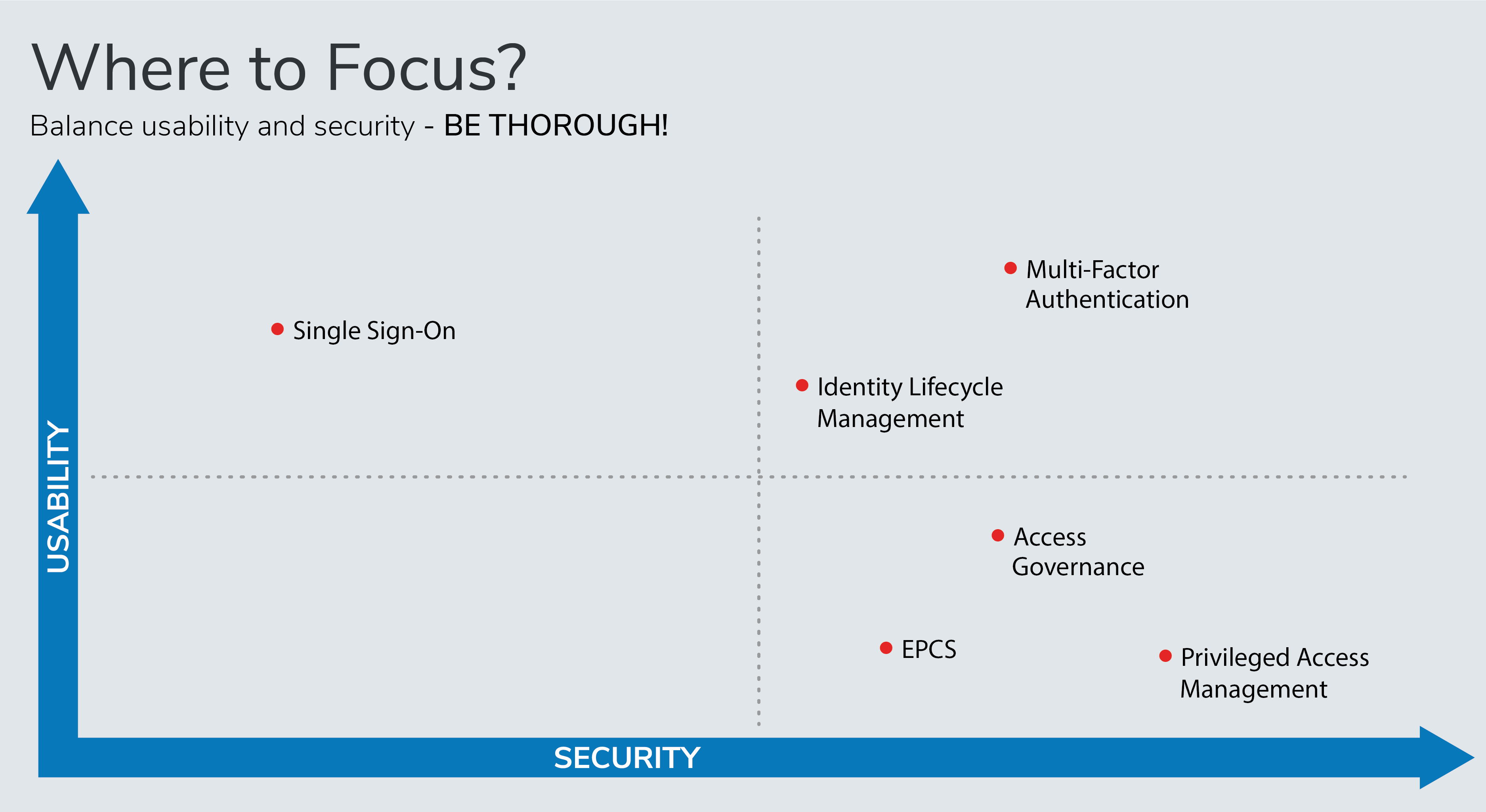
This chart shows how IAM tools allow organizations to balance usability and security. With usability on the vertical axis and security on the horizontal, this visual displays which tenets of IAM are more driven to one side or the other.
For example, Privileged Access Management (PAM) is positioned towards the bottom right because this IAM tenet is more of a healthcare security play. PAM focuses on securing accounts or identities that have a higher level of access, or privileged accounts, by putting more granular controls in place.
On the other hand, SSO is located towards the top left side because it’s primary purpose is enhancing usability. SSO enables clinician workflows and empowers healthcare staff to quickly access the applications and systems required, so their main focus can be on the patient instead. However, SSO does not help organizations to increase their security posture.
Identity Lifecycle Management (ILM) is the most centered IAM tenet on the chart because it strikes a balance between usability and security. ILM ensures identities and accounts created which is important for usability, but it’s also important for healthcare security because it ensures the appropriate actions are taken for any changes, such as a role change where access to certain resources must be adjusted. Moreover, ILM includes the removal of identities across all the services and applications within the organization's ecosystem which is often overlooked and becomes a security gap when left open.
Multi-Factor Authentication (MFA) features the highest security and usability out of any other tenet on the chart. MFA is important because it can be used to set up multiple methods of authentication. So, if one method isn’t working properly, the user can try another method instead of being road blocked, enhancing usability. At the same time, in the event that a user’s credentials are stolen, using a second or third form of verification through MFA can render a cyberattack harmless. When implementing MFA, first consider what your healthcare facility is already using. For example, if you’re using physical badges to gain building access, those same badges can be leveraged to authenticate into systems.
Access Governance centers around the creation and management of policies, which are meant to be restrictive. Another main area of Access Governance is auditing and reporting, so that’s why it makes sense this tenet is low on the usability side, but high for healthcare security.
Similarly, EPCS, or the Electronic Prescribing of Controlled Substances, focuses on compliance and regulatory capabilities as well. In order to prescribe, we have to ensure the clinician is who they say they are, so added controls must be included in that process. As EPCS is being dictated, different states have different requirements and forms of authentication so make sure you know what is required for your state.
When you’re examining which tenets to focus on, think about managing all types of identities, and remember identities are not limited to just employees. IAM extends far beyond a traditional person or identity, and reaches into areas we may not consider such as patient identities, devices, and Application Programming Interfaces (APIs) which need identities associated with them as well.
Evaluate Your Organization and Set Priorities with the IAM Maturity Assessment Tool
The world of IAM is always evolving, especially in healthcare, but it helps to set a foundation so we can take our cybersecurity initiatives to the next level. While IAM is spread across many areas and processes in healthcare organizations, it is ultimately used to enhance usability, while maintaining security. However, certain tools, such as SSO are prevalent in terms of usability, whereas Access Governance, PAM, and EPCS aim to enhance healthcare security.
So, where can you go to find any missing security gaps and establish priorities for your healthcare facility?
We recommend starting with our IAM Maturity Assessment Tool to narrow down your organization’s particular areas of focus.
This short, seven question quiz assesses your organization’s maturity within each IAM tenet and provides actionable steps to take your IAM strategy to the next level.

Comments