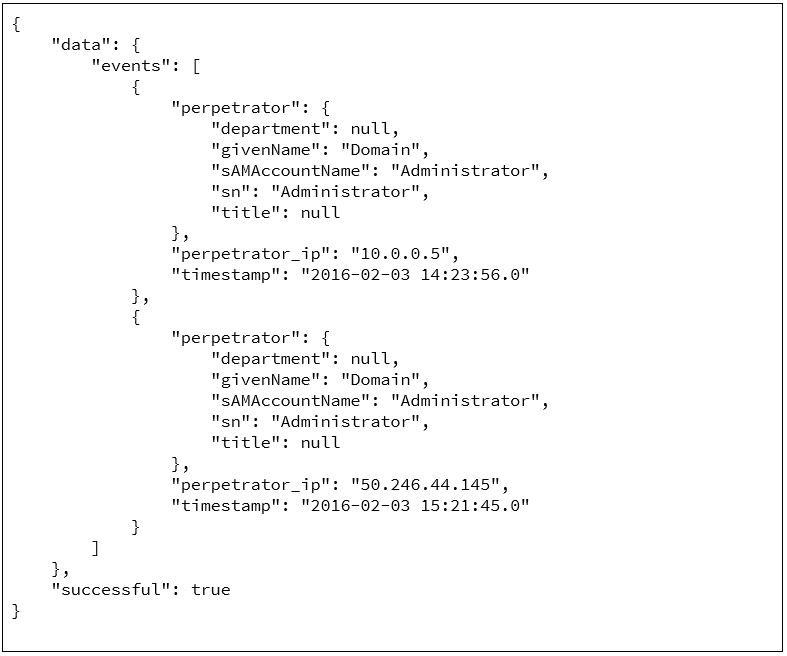
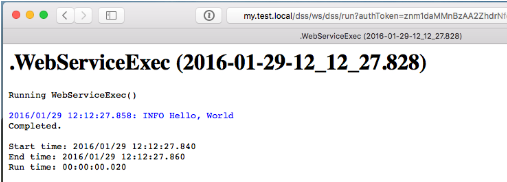
In Part I of our “Building Web Services with RapidConnect” series, I described how to create a simple Web Service using RapidConnect. To summarize, any RapidConnect action set results in having a new Web Service API method. The primary benefit is that as a user, you are limited only by imagination and available data in building powerful Web Services for your own use.
Identity Automation Blog
Don't Stop at Single Sign On
There is no doubt that single sign-on (SSO) capabilities are an important part of any identity and access management (IAM) solution. SSO reduces user frustrations by eliminating the need to keep a list of separate login credentials for individual applications and lowers support costs by helping to reduce the amount of time IT spends addressing login issues and resetting forgotten passwords. Single sign-on can also be utilized for documenting user account activity.
ISTE 2016 Recap: Talking Identity Management, Student Data Rostering, and Student Data Privacy
At the end of June, I joined more than 16,000 ed tech leaders as they converged on Denver, Colorado for a week of idea sharing, collaboration, and networking at the 2016 ISTE Conference & Expo.
Clayton County Public Schools Choose Identity and Access Management Solution from Identity Automation
Looking for the Clayton County Public Schools User Login Page? 
Located in the Atlanta suburb of Jonesboro, Georgia, Clayton County Public Schools (CCPS) is future-forward district with a vision of making the digital classroom a reality for its more than 55,000 students, staff, and administrators. As part of this, CCPS is aggressively working towards district-wide adoption of cloud-based education technology.
Introducing the RapidIdentity Technical Blog Series
Our Technical Support and Product teams are often asked for advice and best practices regarding various technical subjects pertaining to our RapidIdentity software. Over the years, we’ve noticed that certain topics have a habit of popping up more than others. We knew that putting together step-by-step resources on these common topics would not only be educational for our customers, but would also enable them to explore these topics at their own pace.
Building Web Services with RapidConnect Part 1: The Basics
One of the great features of RapidConnect is the flexibility to execute action sets. There are three methods for running your action sets:
Protecting Retail from Security Threats with Workforce IAM
It is a challenging reality of the retail sector that employees are traditionally the weakest link to deterring digital security threats, such as system breaches and data theft. In a complex environment where employee turnover, seasonal workers, a mobile workforce, and shifting roles are a constant challenge, protecting the organization from security threats requires a vigilant approach to access and identity governance.
The Foundation of PCI Compliance: Identity Management Software
The goal of the Payment Card Industry Data Security Standard (PCI) is to protect cardholder information from abuse. While the standard does not make any technology recommendations, its requirements line up with best practices for how payment card information should be handled, communicated, and stored in order to sufficiently secure it.
4 Signs You Need to Modernize Your Identity Management Software
According to Statista, the market for identity and access management is expected to grow to 7.1 billion dollars by the year 2018. This is up from 4.5 billion dollars in 2012; and much of this growth can be attributed to the fact that so many organizations are looking to upgrade their identity management software to better meet the security and workflow needs their company faces.
Unfortunately, there is no odometer on your current identity management solution that tells you it is time for an upgrade. Instead, knowing when you need to look at making a change can be determined by these four key factors.
Identity Automation Allows Organizations to Manage Up to 8 Times More User Identities with Existing Hardware
As we announced in our recent press release, RapidIdentity 4.0 is now available, so I thought I’d discuss what this enhanced functionality and scalability means for our new and existing customers.
current_page_num+2: 34 -